【解析情報】
◆New Satori Botnet Variant Enslaves Thousands of Dasan WiFi Routers (Radware, 2018/02/18)
https://blog.radware.com/security/botnets/2018/02/new-satori-botnet-variant-enslaves-thousands-dasan-wifi-routers/
【ニュース】
◆Satori Botnet Has Sudden Awakening With Over 280,000 Active Bots (BLEEPINGCOMPUTER, 2017/12/05 14:10)
https://www.bleepingcomputer.com/news/security/satori-botnet-has-sudden-awakening-with-over-280-000-active-bots/
◆IoTマルウェア「Satori」攻撃発生、アジアに感染集中か--ワーム型で拡大 (ZDNet, 2017/12/06 19:30)
https://japan.zdnet.com/article/35111546/
◆Huaweiルータの脆弱性突くマルウェア「オキル/サトリ」、世界各地で攻撃発生 (ITmedia, 2017/12/26 07:00)
http://www.itmedia.co.jp/enterprise/articles/1712/26/news060.html
◆SATORI AUTHOR LINKED TO NEW MIRAI VARIANT MASUTA (threatpost, 2018/01/23)
https://threatpost.com/satori-author-linked-to-new-mirai-variant-masuta/129640/
◆A fast-evolving new botnet could take gadgets in your home to the dark side (MIT Technology Review, 2018/01/31)
Satori is built to turn routers, thermostats, and other household devices into zombies.
◆爆速で進化し続ける マルウェア「サトリ」が モノのボットネットを構築中 (ASCII.jp, 2018/02/09 05:57)
http://ascii.jp/elem/000/001/629/1629458/
◆仮想通貨を採掘していたら、ごっそり横取りされました (ASCII.jp, 2018/02/09 09:00)
http://ascii.jp/elem/000/001/626/1626996/
◆マルウェア「Mirai」亜種の活動減退、原因不明も要警戒--IIJ (ZDNet, 2018/02/13 16:35)
https://japan.zdnet.com/article/35114638/
◆Darknet - Satori strikes again (SISSDEN, 2018/02/16)
https://sissden.eu/blog/darknet-satori-dasan
◆New Satori Botnet Variant Enslaves Thousands of Dasan WiFi Routers (Radware, 2018/02/18)
https://blog.radware.com/security/botnets/2018/02/new-satori-botnet-variant-enslaves-thousands-dasan-wifi-routers/
◆警察庁、仮想通貨イーサリアム(ETH)採掘ソフトウェア「Claymore(クレイモア)」を標的としたアクセスの増加等について注意喚起 (VentureTimes, 2018/03/14)
http://venturetimes.jp/cryptocurrency/34421.html
◆ルーターやIoT機器をゾンビ化させる「Satori」の恐怖 (ASCII.jp, 2018/02/23 09:00)
http://ascii.jp/elem/000/001/633/1633271/
◆国内のMirai亜種感染機器からの通信が3月に増加 - 背景に「akuma」 (Security NEXT, 2018/04/20)
http://www.security-next.com/092104
◆Botnets never Die, Satori REFUSES to Fade Away (Netlab(Qihoo 360), 2018/06/15)
http://blog.netlab.360.com/botnets-never-die-satori-refuses-to-fade-away-en/
◆ボットネット構築を行うマルウェア「Satori」の攻撃が急増 新たな亜種マルウェアの拡散を狙う攻撃を日本国内でも観測 (産経新聞, 2018/06/25 14:49)
http://www.sankei.com/economy/news/180625/prl1806250230-n1.html
◆マルウェア「Satori」による攻撃を国内初観測、従来のファイアウォール機能では対応が難しい? (@IT, 2018/06/27 13:00)
http://www.atmarkit.co.jp/ait/articles/1806/27/news083.html
◆Mirai亜種のIoTマルウェア「Okiru」とは? 標的は「ARCプロセッサ」 (TechTarget, 2018/09/04 05:00)
http://techtarget.itmedia.co.jp/tt/news/1809/04/news04.html
【ブログ】
◆国内における Mirai 亜種の感染急増 (2017年11月の観測状況) (IIJ-SECT, 2017/12/07)
https://sect.iij.ad.jp/d/2017/12/074702.html
◆Huawei Routers Exploited to Create New Botnet (Check Point, 2017/12/21)
https://blog.checkpoint.com/2017/12/21/huawei-routers-exploited-create-new-botnet/
◆Huawei router exploit involved in Satori and Brickerbot given away for free on Christmas by Blackhat Santa (Newsky Security, 2017/12/29)
https://blog.newskysecurity.com/huawei-router-exploit-involved-in-satori-and-brickerbot-given-away-for-free-on-christmas-by-ac52fe5e4516
◆Masuta : Satori Creators’ Second Botnet Weaponizes A New Router Exploit. (newskysecurity, 2018/01/23)
https://blog.newskysecurity.com/masuta-satori-creators-second-botnet-weaponizes-a-new-router-exploit-2ddc51cc52a7
◆Satori Botnet Turns IoT Devices Into Zombies By Borrowing Code from Mirai (McAfee, 2018/02/09)
https://securingtomorrow.mcafee.com/business/satori-botnet-turns-iot-devices-zombies-borrowing-code-mirai/
【公開情報】
◆Warning: Satori, a Mirai Branch Is Spreading in Worm Style on Port 37215 and 52869 (360.com, 2017/12/06)
http://blog.netlab.360.com/warning-satori-a-new-mirai-variant-is-spreading-in-worm-style-on-port-37215-and-52869-en/
◆Satori IoT Botnet Variant (Radware, 2018/06/19)
https://security.radware.com/ddos-threats-attacks/threat-advisories-attack-reports/satori-iot-botnet/
【参考画像】

出典: https://www.bleepingcomputer.com/news/security/satori-botnet-has-sudden-awakening-with-over-280-000-active-bots/

出典: http://image.itmedia.co.jp/l/im/enterprise/articles/1712/26/l_ki_okiru02.jpg

出典: https://blog.newskysecurity.com/masuta-satori-creators-second-botnet-weaponizes-a-new-router-exploit-2ddc51cc52a7
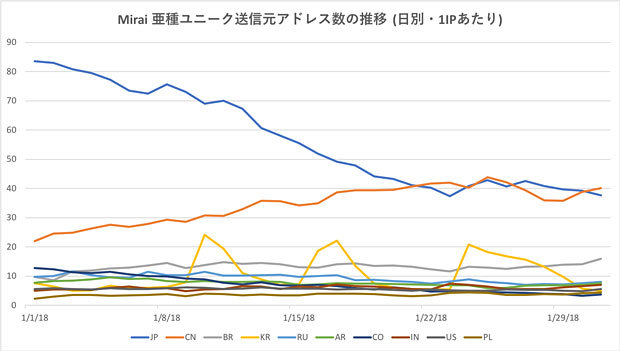
出典: https://japan.zdnet.com/article/35114638/



出典: https://sissden.eu/blog/darknet-satori-dasan

出典: https://blog.radware.com/security/botnets/2018/02/new-satori-botnet-variant-enslaves-thousands-dasan-wifi-routers/

D-Link exploitation attempts
出典: https://security.radware.com/ddos-threats-attacks/threat-advisories-attack-reports/satori-iot-botnet/

ダウンローダー(185.62.190.191)へ誘導する攻撃検知数推移

ダウンローダー(217.61.6.127)へ誘導する攻撃検知数推移
出典: http://www.atmarkit.co.jp/ait/articles/1806/27/news083.html
【インディケータ情報】
■ハッシュ情報(MD5)
| df9c48e8bc7e7371b4744a2ef8b83ddf | hxxp://95.211.123.69/b |
| a7922bce9bb0cf58f305d17ccbc78d98 | hxxp://95.211.123.69/fahwrzadws/okiru.mipsel |
| 37b7c9831334de97c762dff7a1ba7b3f | hxxp://95.211.123.69/fahwrzadws/okiru.arm7 |
| e1411cc1726afe6fb8d09099c5fb2fa6 | hxxp://95.211.123.69/fahwrzadws/okiru.x86 |
| cd4de0ae80a6f11bca8bec7b590e5832 | hxxp://95.211.123.69/fahwrzadws/okiru.x86 |
| 7de55e697cd7e136dbb82b0713a01710 | hxxp://95.211.123.69/fahwrzadws/okiru.mips |
| 797458f9cee3d50e8f651eabc6ba6031 | hxxp://95.211.123.69/fahwrzadws/okiru.m68k |
| 353d36ad621e350f6fce7a48e598662b | hxxp://95.211.123.69/fahwrzadws/okiru.arm |
| 8db073743319c8fca5d4596a7a8f9931 | hxxp://95.211.123.69/fahwrzadws/okiru.sparc |
| 0a8efeb4cb15c5b599e0d4fb9faba37d | hxxp://95.211.123.69/fahwrzadws/okiru.powerpc |
| 08d48000a47af6f173eba6bb16265670 | hxxp://95.211.123.69/fahwrzadws/okiru.x86_64 |
| e9038f7f9c957a4e1c6fc8489994add4 | hxxp://95.211.123.69/fahwrzadws/okiru.superh |
(以上は 360.com の情報。 引用元は http://blog.netlab.360.com/warning-satori-a-new-mirai-variant-is-spreading-in-worm-style-on-port-37215-and-52869-en/)