【要点】
◎北朝鮮の標的型攻撃組織。北朝鮮・国家安全保障省(MSS)内の一要素
【目次】
概要
【辞書】
◆APT37 (FireEye)
https://www.fireeye.com/current-threats/apt-groups.html
◆APT37 (Malpedia)
https://malpedia.caad.fkie.fraunhofer.de/actor/apt37
◆APT37とは【用語集詳細】 (SOMPO CYBER SECURITY)
https://www.sompocybersecurity.com/column/glossary/apt37
【別名】
| 攻撃組織名 | 命名組織 |
|---|---|
| APT37 | FireEye |
| ATK4 | |
| Dark Sleeper | |
| FreeMilk | |
| G0067 | |
| Group123 | |
| InkySquid | |
| Moldy Pisces | |
| Reaper | |
| Red Eyes | |
| Ricochet Chollima | |
| ScarCruft | Kaspersky |
| Sun Team | |
| Venus 121 |
【Operation名】
| Operation名 | 命名組織 |
|---|---|
| Operation Daybreak | |
| Operation Erebus |
【概要】
| 項目 | 内容 |
|---|---|
| 攻撃対象国 | 日本、ロシア、ネパール、韓国、中国、インド、クウェート、ルーマニア |
【最新情報】
◆APT37 hackers deploy new FadeStealer eavesdropping malware (BleepingComputer, 2023/06/21 16:16)
[APT37ハッカー、新たな盗聴マルウェア「FadeStealer」を展開]
https://www.bleepingcomputer.com/news/security/apt37-hackers-deploy-new-fadestealer-eavesdropping-malware/
⇒ https://malware-log.hatenablog.com/entry/2023/06/21/000000_4
記事
【ニュース】
■2016年
◆Flashゼロデイ攻撃、APTグループ「ScarCruft」関与か - EMETで回避可能 (Security NEXT, 2016/06/15)
http://www.security-next.com/070993
⇒ http://malware-log.hatenablog.com/entry/2016/06/15/000000_1
◆APT Group Uses Flash Zero-Day to Attack High-Profile Targets (SECURITYWEEK, 2016/06/15)
http://www.securityweek.com/apt-group-uses-flash-zero-day-attack-high-profile-targets
⇒ http://malware-log.hatenablog.com/entry/2018-06-15/000000
◆Adobe Flash Player 22.0.0.192 release fixes the Flash Player zero-day vulnerability (CVE-2016-4171) exploited by the APT group dubbed ScarCruft. (Security Affairs, 2016/06/19)
http://securityaffairs.co/wordpress/48531/cyber-crime/flash-zero-day-scarcruft.html
⇒ http://malware-log.hatenablog.com/entry/2016/06/19/000000_1
■2018年
◆North Korean hackers belonging to the North Korea Group 123 have conducted at least six different massive malware campaigns during 2017. (Security Affairs, 2018/01/18)
http://securityaffairs.co/wordpress/67895/hacking/north-korea-group-123.html
⇒ http://malware-log.hatenablog.com/entry/2018/01/18/000000_8
◆Cisco and FireEye Pointing Finger at North Korea Hacking Group For Adobe Flash 0-Day In The Wild (Security Affairs, 2018/02/05)
http://securityaffairs.co/wordpress/68718/hacking/north-korea-adobe-flash-0day.html
⇒ http://malware-log.hatenablog.com/entry/2018/02/05/000000_2
◆THE TOOLSET OF AN ELITE NORTH KOREAN HACKER GROUP ON THE RISE (WIRED, 2018/02/20)
https://www.wired.com/story/north-korean-hacker-group-apt37/
⇒ http://malware-log.hatenablog.com/entry/2018/02/20/000000_5
◆North Korean APT Group tracked as APT37 broadens its horizons (Security Affairs, 2018/02/21)
http://securityaffairs.co/wordpress/69339/apt/apt37-broadens-horizons.html
⇒ http://malware-log.hatenablog.com/entry/2018/02/21/000000_8
◆北朝鮮ハッカー「APT37」、日本攻撃 制裁情報狙い、米企業分析 (産経新聞, 2018/02/21 07:20)
http://www.sankei.com/world/news/180221/wor1802210005-n1.html
⇒ http://malware-log.hatenablog.com/entry/2018/02/21/000000
◆北朝鮮 ハッカー集団、国家ぐるみで日本に攻撃か (毎日新聞, 2018/02/22)
https://mainichi.jp/articles/20180222/ddm/007/030/070000c
⇒ http://malware-log.hatenablog.com/entry/2018/02/22/000000_4
◆日本も攻撃対象に、北朝鮮ハッカー集団「APT37」が活発化 (サイバーセキュリティ.com, 2018/02/23)
https://cybersecurity-jp.com/news/22473
⇒ http://malware-log.hatenablog.com/entry/2018/02/23/000000_7
◆「サイバー攻撃が起きる度に北に押し付け」…北朝鮮メディアが日米を非難 (Japan Daily NK, 2018/03/08)
https://dailynk.jp/archives/106907
⇒ http://malware-log.hatenablog.com/entry/2018/03/08/000000_2
◆北が躍起になるサイバー諜報活動 首脳会談前に情報集め?金正恩氏の焦り見え隠れ (産経新聞, 2018/04/10 07:00)
https://www.sankei.com/world/news/180410/wor1804100001-n1.html
⇒ http://malware-log.hatenablog.com/entry/2018/04/10/000000_1
◆北朝鮮悪用のFlash脆弱性、広く悪用される状態に - 海外中心に攻撃が拡大、国内でも (Security NEXT, 2018/04/20)
http://www.security-next.com/092519
⇒ http://malware-log.hatenablog.com/entry/2018/04/20/000000_2
◆北朝鮮脱北者を狙ったGoogle Playのマルウェア (ASCII.jp, 2018/05/18 19:00)
http://ascii.jp/elem/000/001/678/1678970/
⇒ http://malware-log.hatenablog.com/entry/2018/05/18/000000_3
◆REDDAWN ESPIONAGE CAMPAIGN SHOWS MOBILE APTS ON THE RISE (Threatpost, 2018/05/18 08:42)
https://threatpost.com/reddawn-espionage-campaign-shows-mobile-apts-on-the-rise/132081/
⇒ http://malware-log.hatenablog.com/entry/2018/05/18/000000_2
◆NOKKI Almost Ties the Knot with DOGCALL: Reaper Group Uses New Malware to Deploy RAT (paloalto, 2018/10/01 08:00)
https://researchcenter.paloaltonetworks.com/2018/10/unit42-nokki-almost-ties-the-knot-with-dogcall-reaper-group-uses-new-malware-to-deploy-rat/
⇒ http://malware-log.hatenablog.com/entry/2018/10/01/000000_1
■2019年
◆北朝鮮の“国家支援型”サイバー攻撃グループ、日本を狙う「APT37」と金融機関を標的にする「APT38」 (Internet Watch, 2019/04/23 12:36)
https://internet.watch.impress.co.jp/docs/news/1181712.html
⇒ https://malware-log.hatenablog.com/entry/2019/04/23/000000_7
◆ScarCruft APT Adds Bluetooth Harvester to its Malware Bag of Tricks (ThreatPost, 2019/05/13 12:46)
[ScarCruft APTがBluetooth Harvesterをマルウェアの技法に追加]
https://threatpost.com/scarcruft-apt-bluetooth-harvester/144643/
https://malware-log.hatenablog.com/entry/2019/05/13/000000_13
◆サイバー犯罪グループ「ScarCruft」が、接続されたBluetoothデバイスを識別するマルウェアなどで情報収集を強化 (時事通信, 2019/05/20 16:40)
https://www.jiji.com/jc/article?k=000000130.000011471
⇒ https://malware-log.hatenablog.com/entry/2019/05/20/000000_1
■2021年
◆誰がサイバー攻撃を仕掛けるのか? 日本を狙う11の主な攻撃グループ (Codebook, 2021/12/17 05:30)
https://codebook.machinarecord.com/15746/
⇒ https://malware-log.hatenablog.com/entry/2021/12/17/000000_14
■2022年
◆North Korean hackers targeting journalists with novel malware (BleepingComputer, 2022/04/25)
[北朝鮮のハッカーが新型マルウェアでジャーナリストを標的に]
https://www.bleepingcomputer.com/news/security/north-korean-hackers-targeting-journalists-with-novel-malware/
⇒ https://malware-log.hatenablog.com/entry/2022/04/25/000000_2
◆North Korean hackers attack EU targets with Konni RAT malware (BleepingComputer, 2022/07/23 12:08)
[北朝鮮のハッカーがRATマルウェア「Konni」でEUの標的を攻撃]
https://www.bleepingcomputer.com/news/security/north-korean-hackers-attack-eu-targets-with-konni-rat-malware/
⇒ https://malware-log.hatenablog.com/entry/2022/07/23/000000
◆Nation-state Hackers Target Journalists with Goldbackdoor Malware (ThreatPost, 2022/04/26 07:38)
https://threatpost.com/hackers-target-journalists-goldbackdoor/179389/
⇒ https://malware-log.hatenablog.com/entry/2022/04/26/000000_5
◆北朝鮮のサイバー犯罪グループ「APT37」がInternet Explorerのゼロデイ脆弱性を突く攻撃を行っていたと判明 (Gigazine, 2022/12/08)
https://gigazine.net/news/20221208-north-korean-apt37-internet-explorer-exploit/
⇒ https://malware-log.hatenablog.com/entry/2022/12/08/000000_1
■2023年
◆ステガノグラフィ技術を使ったハングル(HWP)マルウェア:RedEyes(ScarCruft) (Ahnlab, 2023/02/14)
https://asec.ahnlab.com/ko/47622/
⇒ https://malware-log.hatenablog.com/entry/2023/02/14/000000_3
◆North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware (The Hacker News, 2023/02/15)
[北朝鮮のAPT37、新型マルウェア「M2RAT」で韓国を標的にする]
https://thehackernews.com/2023/02/north-koreas-apt37-targeting-southern.html
⇒ https://malware-log.hatenablog.com/entry/2023/02/15/000000_1
◆APT37 hackers deploy new FadeStealer eavesdropping malware (BleepingComputer, 2023/06/21 16:16)
[APT37ハッカー、新たな盗聴マルウェア「FadeStealer」を展開]
https://www.bleepingcomputer.com/news/security/apt37-hackers-deploy-new-fadestealer-eavesdropping-malware/
⇒ https://malware-log.hatenablog.com/entry/2023/06/21/000000_4
◆North Korean hackers 'ScarCruft' breached Russian missile maker (BleepingComputer, 2023/08/07 10:57)
[北朝鮮のハッカー「ScarCruft」がロシアのミサイルメーカーに侵入]
https://www.bleepingcomputer.com/news/security/north-korean-hackers-scarcruft-breached-russian-missile-maker/
⇒ https://malware-log.hatenablog.com/entry/2023/08/07/000000_1
■2024年
◆北朝鮮のハッカーが「Internet Explorer」のゼロデイ脆弱性を悪用してマルウェア攻撃を仕掛ける (Gigazine, 2024/10/18 17:00)
https://gigazine.net/news/20241018-internet-explorer-zero-day-malware/
⇒ https://malware-log.hatenablog.com/entry/2024/10/18/000000_3
【ブログ】
■2016年
◆CVE-2016-4171 – Adobe Flash Zero-day used in targeted attacks (SecureList, 2016/06/14)
https://securelist.com/cve-2016-4171-adobe-flash-zero-day-used-in-targeted-attacks/75082/
⇒ http://malware-log.hatenablog.com/entry/2016/06/14/000000_10
◆Operation Daybreak (SECURELIST, 2016/06/17)
Flash zero-day exploit deployed by the ScarCruft APT Group
https://securelist.com/blog/research/75100/operation-daybreak/
⇒ http://malware-log.hatenablog.com/entry/2016/06/17/000000_7
■2018年
◆Korea In The Crosshairs (Talos, 2018/01/16)
http://blog.talosintelligence.com/2018/01/korea-in-crosshairs.html
⇒ http://malware-log.hatenablog.com/entry/2018/01/16/000000_8
◆APT37 (Reaper): The Overlooked North Korean Actor (FireEye, 2018/02/20)
https://www.fireeye.com/blog/threat-research/2018/02/apt37-overlooked-north-korean-actor.html
⇒ http://malware-log.hatenablog.com/entry/2018/02/20/000000_7
◆北朝鮮のサイバー攻撃グループ「APT37」が活発化 (THE ZERO/ONE, 2018/03/02)
https://the01.jp/p0006529/
⇒ http://malware-log.hatenablog.com/entry/2018/03/02/000000_3
◆NavRAT Uses US-North Korea Summit As Decoy For Attacks In South Korea (Talos(CISCO), 2018/05/31)
https://blog.talosintelligence.com/2018/05/navrat.html?m=1
⇒ http://malware-log.hatenablog.com/entry/2018/05/31/000000_5
■2022年
◆Internet Explorer 0-day exploited by North Korean actor APT37 (Google, 2022/12/07)
[Internet Explorerの0-dayを悪用した北朝鮮のアクターAPT37の攻撃について]
https://blog.google/threat-analysis-group/internet-explorer-0-day-exploited-by-north-korean-actor-apt37/
⇒ https://malware-log.hatenablog.com/entry/2022/12/07/000000_2
■2024年
◆APT45: North Korea’s Digital Military Machine (Mandiant(Google), 2024/07/26)
[APT45:北朝鮮のデジタル軍事マシン]
https://cloud.google.com/blog/topics/threat-intelligence/apt45-north-korea-digital-military-machine?hl=en
⇒ https://malware-log.hatenablog.com/entry/2024/07/26/000000_1
【公開情報】
■2016年
◆Fear The Reaper - North Korean Group APT37
https://exchange.xforce.ibmcloud.com/collection/Fear-The-Reaper-North-Korean-Group-APT37-dc96e8bdff7573efb87d43d7584c1fbc
⇒ https://malware-log.hatenablog.com/entry/2016/06/15/000000_2
【資料】
■2018年
◆APT37 (REAPER) (FireEye, 2018/02/20)
https://www2.fireeye.com/rs/848-DID-242/images/rpt_APT37.pdf
https://web.archive.org/web/20180404190945/https://www2.fireeye.com/rs/848-DID-242/images/rpt_APT37.pdf
https://paper.bobylive.com/Security/APT_Report/APT-37.pdf
https://services.google.com/fh/files/misc/apt37-reaper-the-overlooked-north-korean-actor.pdf
⇒ http://malware-log.hatenablog.com/entry/2018/02/20/000000_6
◆APT37 (REAPER) (FireEye, 2018/02/21)
知られざる北朝鮮の攻撃グループ
https://www2.fireeye.com/rs/848-DID-242/images/rpt-apt37-JP.pdf
⇒ http://malware-log.hatenablog.com/entry/2018/02/21/000000_9
【図表】
■2018年
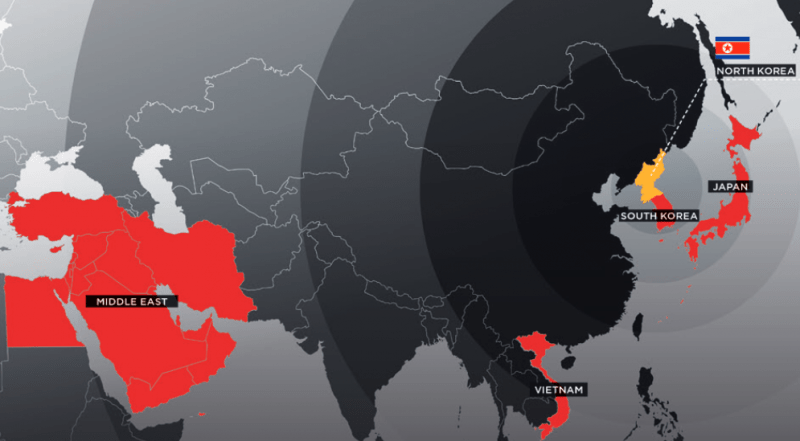
APT37の標的先
出典: https://the01.jp/p0006529/
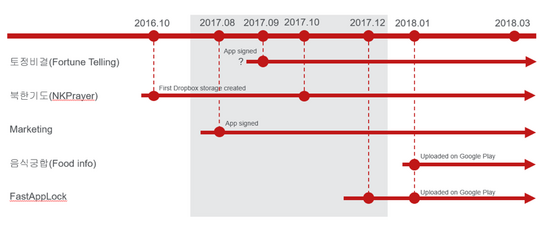
「Sun Team(APT37)」により開発されたマルウェアのタイムライン
出典: http://ascii.jp/elem/000/001/678/1678970/
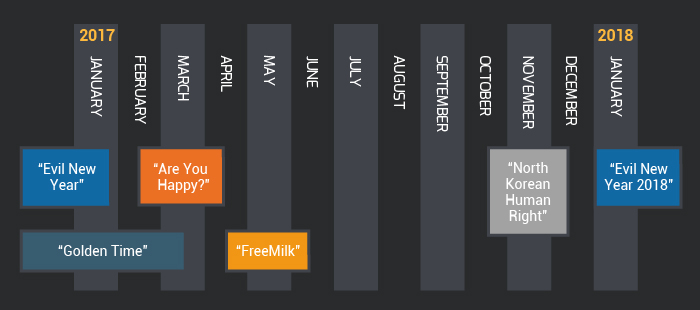
出典: https://blog.talosintelligence.com/2018/01/korea-in-crosshairs.html
関連情報
【関連まとめ記事】
◆標的型攻撃組織 / APT (まとめ)
https://malware-log.hatenablog.com/entry/APT
【インディケータ情報】
■ハッシュ情報(Sha256)
| Sha256 | 備考 |
|---|---|
| e5f191531bc1c674ea74f8885449f4d934d5f1aa7fd3aaa283fe70f9402b9574 | 悪質なHWP |
| 4f06eaed3dd67ce31e7c8258741cf727964bd271c3590ded828ad7ba8d04ee57 | NavRAT |
(以上は Talosの情報: 引用元は https://blog.talosintelligence.com/2018/05/navrat.html?m=1)
■ハッシュ情報(Sha256) - 2016 NavRATサンプル
- 0257d187be69b9bee0a731437bf050d56d213b50a6fd29dd6664e7969f286ef
(以上は Talosの情報: 引用元は https://blog.talosintelligence.com/2018/05/navrat.html?m=1)
【インディケータ情報】
■ ハッシュ情報(Sha256) - Golden Time
| 種別 | Sha256 |
|---|---|
| Maldoc | 7d163e36f47ec56c9fe08d758a0770f1778fa30af68f39aac80441a3f037761e |
| Maldoc | 5441f45df22af63498c63a49aae82065086964f9067cfa75987951831017bd4f |
| ROKRAT | cd166565ce09ef410c5bba40bad0b49441af6cfb48772e7e4a9de3d646b4851c |
| ROKRAT | 051463a14767c6477b6dacd639f30a8a5b9e126ff31532b58fc29c8364604d00 |
■ ハッシュ情報(Sha256) - Evil New Year
| 種別 | Sha256 |
|---|---|
| Maldoc | 281828d6f5bd377f91c6283c34896d0483b08ac2167d34e981fbea871893c919 |
| Dropped | 95192de1f3239d5c0a7075627cf9845c91fd397796383185f61dde893989c08a |
| Dropped | 7ebc9a1fd93525fc42277efbccecf5a0470a0affbc4cf6c3934933c4c1959eb1 |
| Dropped | 6c372f29615ce8ae2cdf257e9f2617870c74b321651e9219ea16847467f51c9f |
| Dropped | 19e4c45c0cd992564532b89a4dc1f35c769133167dc20e40b2a41fccb881277b |
| Dropped | 3a0fc4cc145eafe20129e9c53aac424e429597a58682605128b3656c3ab0a409 |
| Dropped | 7d8008028488edd26e665a3d4f70576cc02c237fffe5b8493842def528d6a1d8 |
| Unpacked | 7e810cb159fab5baccee7e72708d97433d92ef6d3ef7d8b6926c2df481ccac2f |
| Unpacked | 21b098d721ea88bf237c08cdb5c619aa435046d9143bd4a2c4ec463dcf275cbe |
| Unpacked | 761454dafba7e191587735c0dc5c6c8ab5b1fb87a0fa44bd046e8495a27850c7 |
| Unpacked | 3d442c4457cf921b7a335c0d7276bea9472976dc31af94ea0e604e466596b4e8 |
| Unpacked | 930fce7272ede29833abbfb5df4e32eee9f15443542434d7a8363f7a7b2d1f00 |
| Unpacked | 4b20883386665bd205ac50f34f7b6293747fd720d602e2bb3c270837a21291b4 |
| Unpacked | f080f019073654acbe6b7ab735d3fd21f8942352895890d7e8b27fa488887d08 |
■ ハッシュ情報(Sha256) - Are You Happy?
| 種別 | Sha256 |
|---|---|
| Wiper | 6332c97c76d2da7101ad05f501dc1188ac22ce29e91dab6d0c034c4a90b615bd |
■ ハッシュ情報(Sha256) - FreeMilk
| 種別 | Sha256 |
|---|---|
| Office | f1419cde4dd4e1785d6ec6d33afb413e938f6aece2e8d55cf6328a9d2ac3c2d0 |
| HTA | a585849d02c94e93022c5257b162f74c0cdf6144ad82dd7cf7ac700cbfedd84f |
| JS | 1893af524edea4541c317df288adbf17ae4fcc3a30d403331eae541281c71a3c |
| PoohMilk | 35273d6c25665a19ac14d469e1436223202be655ee19b5b247cb1afef626c9f2 |
| Freenki | 7f35521cdbaa4e86143656ff9c52cef8d1e5e5f8245860c205364138f82c54df |
| Freenki 2016 | 99c1b4887d96cb94f32b280c1039b3a7e39ad996859ffa6dd011cf3cca4f1ba5 |
■ ハッシュ情報(Sha256) - North Korean Human Rights
| 種別 | Sha256 |
|---|---|
| Maldoc | 71e26822421f7ed2e34cc092eaeba8a504b5d576c7fd54aa6975c2e2db0f824 |
| Dropper | a29b07a6fe5d7ce3147dd7ef1d7d18df16e347f37282c43139d53cce25ae7037 |
| Dropper | eb6d25e08b2b32a736b57f8df22db6d03dc82f16da554f4e8bb67120eacb1d14 |
| Dropper | 9b383ebc1c592d5556fec9d513223d4f99a5061591671db560faf742dd68493f |
| ROKRAT | b3de3f9309b2f320738772353eb724a0782a1fc2c912483c036c303389307e2e |
■ ハッシュ情報(Sha256) - Evil New Year 2018
| 種別 | Sha256 |
|---|---|
| Maldoc | f068196d2c492b49e4aae4312c140e9a6c8c61a33f61ea35d74f4a26ef263ead |
| PNG | bdd48dbed10f74f234ed38908756b5c3ae3c79d014ecf991e31b36d957d9c950 |
| ROKRAT | 3f7827bf26150ec26c61d8dbf43cdb8824e320298e7b362d79d7225ab3d655b1 |