== 【目次】==
概要
【別名】
| 組織名 | 備考 |
|---|---|
| Bald Knight | |
| Bronze Butler | Dell Secureworks, (Trendmicro) |
| NCPH | iDefense |
| Nian | |
| RedBaldKnight | Trendmicro |
| The Bald Knight Rises | kaspersky |
| Tick | Symantec, (Trendmicro), Ahnlab |
【辞書】
◆BRONZE BUTLER (ATT&CK)
https://attack.mitre.org/groups/G0060/
◆Network Crack Program Hacker Group(NCPH) (Wikipedia)
https://en.wikipedia.org/wiki/Network_Crack_Program_Hacker_Group
⇒ http://malware-log.hatenablog.com/entry/NCPH
◆Tick (Malpedia)
https://malpedia.caad.fkie.fraunhofer.de/actor/tick
【使用マルウェア】
■ダウンローダー
| マルウェア名 | 別名 | 備考 |
|---|---|---|
| Wali | ダウンローダー | |
| Bisodown | Cpycat / HomamDownloader / Homan | ダウンローダー, 2014/04に発見 |
| Gofarer | ダウンローダー, 2015~2019 | |
| ABK Downloader | ||
| Avirra Downloader |
■RAT
| マルウェア名 | 別名 | 備考 |
|---|---|---|
| XXMM | KVNDM / Minzen / Murim / ShadowWali / Wali / Wrim | RAT |
| Daserf | Muirim / Nioupale / Postbot | RAT |
| Datper | RAT | |
| NamwlessHdoor | RAT | |
| Netboy | Domino / Invader | RAT |
| Ninezero | 9002 | RAT |
■未整理
| マルウェア名 | 別名 | 備考 |
|---|---|---|
| BBK | ||
| doc_II | ||
| Pretender | ||
| Hidefloder | ||
| Build_down | ||
| Lilith | ||
| Down_new | ||
| Casper | ||
| Avenger |
【概要】
| 項目 | 内容 |
|---|---|
| 攻撃対象 | 日本、韓国 |
【最新情報】
◆中国共産党員を書類送検へ JAXAにサイバー攻撃 (共同通信, 2021/04/20 11:04)
https://www.msn.com/ja-jp/news/world/jaxa%E3%81%AB%E3%82%B5%E3%82%A4%E3%83%90%E3%83%BC%E6%94%BB%E6%92%83%E3%81%8B-%E4%B8%AD%E5%9B%BD%E7%B1%8D%E3%81%AE%E7%94%B7%E6%80%A7%E3%82%92%E6%9B%B8%E9%A1%9E%E9%80%81%E6%A4%9C%E3%81%B8/ar-BB1fPxFO
◆サイバー攻撃 電機メーカーや大学も 中国人民解放軍指示か (NHK, 2021/04/20 12:34)
https://www3.nhk.or.jp/shutoken-news/20210420/1000063263.html
https://malware-log.hatenablog.com/entry/2021/04/20/000000_5
◆サイバー攻撃 中国共産党員の男ら警視庁事情聴取も その後出国 (NHK, 2021/04/20 18:58)
https://www3.nhk.or.jp/news/html/20210420/k10012986251000.html
⇒ https://malware-log.hatenablog.com/entry/2021/04/20/000000_4
◆サイバー攻撃で書類送検に中国反発「証拠示すべき」 (テレ朝, 2021/04/20 19:24)
https://news.tv-asahi.co.jp/news_international/articles/000213592.html
⇒ https://malware-log.hatenablog.com/entry/2021/04/20/000000_6
記事
【ニュース】
■2008年
◆中国・ロシアのハッカー最新事情 (ITPro, 2008/01/07)
http://itpro.nikkeibp.co.jp/article/COLUMN/20071225/290187/?rt=nocnt
⇒ http://malware-log.hatenablog.com/entry/2008/01/07/000000
■2015年
◆Detecting Daserf variants using Security Analytics (RSA, 2015/09/28)
https://community.rsa.com/community/products/netwitness/blog/2015/09/28/detecting-daserf-variants-using-security-analytics
⇒ http://malware-log.hatenablog.com/entry/2015/09/28/000000
■2016年
◆Tick Cyber-Espionage Group Targets Japanese Companies with Daserf Backdoors (Softpedia, 2016/04/29)
http://news.softpedia.com/news/tick-cyber-espionage-group-targets-japanese-companies-with-daserf-backdoors-503555.shtml
⇒ http://malware-log.hatenablog.com/entry/2016/04/29/000000_1
◆TICK CYBERESPIONAGE GROUP ZEROS IN ON JAPAN (Information Security Newspaper, 2016/04/30)
http://www.securitynewspaper.com/2016/04/30/tick-cyberespionage-group-zeros-japan/
⇒ http://malware-log.hatenablog.com/entry/2016/04/30/000000
◆10年前から密かに活動していたサイバースパイ集団「Tick」、日本のテクノロジー系/水産工学系/報道系の特定企業に集中攻撃 (Internet Watch, 2016/05/06 19:47)
http://internet.watch.impress.co.jp/docs/news/756214.html
⇒ http://malware-log.hatenablog.com/entry/2016/05/06/000000_1
◆ラック、マルウェア「Daserf」の実態レポート「日本の重要インフラ事業者を狙った攻撃者」を公開 (EnterpriseZine, 2016/08/02 15:00)
https://enterprisezine.jp/article/detail/8333
⇒ http://malware-log.hatenablog.com/entry/2016/08/02/000000
◆重要インフラを狙うマルウェア「Daserf」、長期間標的組織に潜伏の可能性(ラック) (NetSecurity, 2016/08/03)
http://scan.netsecurity.ne.jp/article/2016/08/03/38799.html
⇒ http://malware-log.hatenablog.com/entry/2016/08/03/000000_2
■2017年
◆日本に精通した標的型攻撃「BRONZE BUTLER」の詳細レポートを公開(SecureWorks) (NetSecurity, 2017/06/23)
https://scan.netsecurity.ne.jp/article/2017/06/26/39888.html
⇒ http://malware-log.hatenablog.com/entry/2017/06/23/000000
◆Tick threat group linked to multiple malware families (SCmedia, 2017/07/25)
https://www.scmagazine.com/tick-threat-group-linked-to-multiple-malware-families/article/677249/
⇒ http://malware-log.hatenablog.com/entry/2017/07/25/000000_7
◆日本企業を狙う中国のサイバースパイ集団、知的財産や製品情報が被害に (ITmedia, 2017/10/16 08:45)
http://www.itmedia.co.jp/enterprise/articles/1710/16/news050.html
⇒ http://malware-log.hatenablog.com/entry/2017/10/16/000000_10
◆日本の製造業や重工業を狙うサイバーグループ「BRONZE BUTLER」に注意 (マイナビニュース, 2017/10/17)
http://news.mynavi.jp/news/2017/10/17/127/
⇒ http://malware-log.hatenablog.com/entry/2017/10/17/000000_11
◆モバイルWi-Fiルーターがマルウェアの感染経路になっていた! 日本を狙った「XXMM」亜種の特徴的な感染経路 (Internet Watch, 2017/12/27)
活動が続く「The Bald Knight Rises」の洗練された攻撃手法、カスペルスキーが解説
https://internet.watch.impress.co.jp/docs/news/1099223.html
⇒ http://malware-log.hatenablog.com/entry/2017/12/27/000000
■2018年
◆セキュアUSBメモリを使うマルウェア攻撃、Windows XPや2003を標的に (ZDNet, 2018/06/25 15:50)
https://japan.zdnet.com/article/35121409/
⇒ http://malware-log.hatenablog.com/entry/2018/06/25/000000
◆Tick APTハッキンググループ、韓国の防衛産業が作成したセキュリティUSBターゲットに攻撃 (Dailysecu, 2018/06/27 22:07)
https://www.dailysecu.com/news/articleView.html?idxno=35901
⇒ https://malware-log.hatenablog.com/entry/2018/06/27/000000_10
■2019年
◆攻撃グループ「Tick」、資産管理ソフトへの脆弱性攻撃を継続 - 標的型攻撃も (Security NEXT, 2019/02/22)
http://www.security-next.com/102741
⇒ http://malware-log.hatenablog.com/entry/2019/02/22/000000_1
◆攻撃集団はつながっている―サイバーインテリジェンス専門家が解説する「技術偵察の実態」 (Enterprize Zine, 2019/07/29 07:00)
https://enterprisezine.jp/article/detail/12300
⇒ https://malware-log.hatenablog.com/entry/2019/07/29/000000_4
■2020年
◆【独自】三菱電機にサイバー攻撃 防衛などの情報流出か (朝日新聞, 2020/01/20 05:00)
https://www.asahi.com/articles/ASN1M6VDSN1MULFA009.html
⇒ https://malware-log.hatenablog.com/entry/2020/01/20/000000
◆【独自】狙いは中間管理職の端末 三菱電機を周到に攻撃 (朝日新聞, 2020/01/20)
https://www.asahi.com/articles/ASN1M6WRJN1MULFA00B.html
⇒ https://malware-log.hatenablog.com/entry/2020/01/20/000000_1
◆標的は日韓企業、暗躍する中国ハッカー集団Tick (日経新聞, 2020/01/20 21:01)
https://www.nikkei.com/article/DGXMZO54623610Q0A120C2EA1000/
⇒ https://malware-log.hatenablog.com/entry/2020/01/20/000000_3
◆三菱電機にサイバー攻撃! 中国系集団関与か 朝日新聞報道 サイバー防衛隊初代隊長・佐藤雅俊氏「氷山の一角」 (Zakzak, 20120/01/20)
https://www.zakzak.co.jp/soc/news/200120/dom2001200009-n1.html
⇒ https://malware-log.hatenablog.com/entry/2020/01/20/000000_4
◆Mitsubishi Electric discloses security breach, China is main suspect (ZDNet, 2020/01/20 10:27 GMT)
https://www.zdnet.com/article/mitsubishi-electric-discloses-security-breach-china-is-main-suspect/
⇒ https://malware-log.hatenablog.com/entry/2020/01/20/000000_9
◆三菱電機にサイバー攻撃「中国系ハッカー集団Tick」の恐るべき正体 (現代ビジネス, 2020/01/21 )
https://gendai.ismedia.jp/articles/-/69918
⇒ https://malware-log.hatenablog.com/entry/2020/01/21/000000_2
◆日本企業を狙うサイバー攻撃集団「Tick」とは何者か? (マイナビニュース, 2020/01/21 14:40)
https://news.mynavi.jp/article/20200121-957754/
⇒ https://malware-log.hatenablog.com/entry/2020/01/21/000000_3
◆【独自】サイバー攻撃4集団 標的の分野・時期は様々 (朝日新聞, 2020/01/22 05:00)
https://digital.asahi.com/articles/ASN1P6V0QN1PUTIL02W.html
⇒ https://malware-log.hatenablog.com/entry/2020/01/22/000000
◆三菱電機、複数の中国系ハッカー集団から攻撃か (朝日新聞, 2020/01/22 05:00)
https://digital.asahi.com/articles/ASN1P6TGLN1PUTIL02V.html?iref=comtop_8_02
⇒ https://malware-log.hatenablog.com/entry/2020/01/22/000000_1
◆1年がかりで組織に潜入…秘密情報狙うハッカー集団の“地味なチームプレー” (AERA, 2020/02/12 17:00)
https://dot.asahi.com/aera/2020021000061.html?page=1
⇒ https://malware-log.hatenablog.com/entry/2020/02/12/000000
◆中国の「国営ハッカー」に、日本一のセキュリティ企業が丸裸の衝撃 (週刊現代, 2020/02/19)
https://malware-log.hatenablog.com/entry/2020/02/19/000000
⇒ https://gendai.ismedia.jp/articles/-/70325
◆中国ハッカーに握られた社内PC 特命チーム暗闘の全貌 (朝日新聞, 2020/05/08 07:00)
https://digital.asahi.com/articles/ASN544T17N52ULZU00F.html
⇒ https://malware-log.hatenablog.com/entry/2020/05/08/000000_1
◆Japan investigates potential leak of prototype missile data in Mitsubishi hack (ZDNet, 2020/05/21 11:21 GMT)
The country is analyzing how such a leak could impact national security.
https://www.zdnet.com/article/japan-investigates-potential-leak-of-prototype-missile-design-in-mitsubishi-hack/
⇒ https://malware-log.hatenablog.com/entry/2020/05/21/000000_3
■2021年
◆中国共産党員を書類送検へ JAXAにサイバー攻撃 (共同通信, 2021/04/20 11:04)
https://www.msn.com/ja-jp/news/world/jaxa%E3%81%AB%E3%82%B5%E3%82%A4%E3%83%90%E3%83%BC%E6%94%BB%E6%92%83%E3%81%8B-%E4%B8%AD%E5%9B%BD%E7%B1%8D%E3%81%AE%E7%94%B7%E6%80%A7%E3%82%92%E6%9B%B8%E9%A1%9E%E9%80%81%E6%A4%9C%E3%81%B8/ar-BB1fPxFO
◆サイバー攻撃 電機メーカーや大学も 中国人民解放軍指示か (NHK, 2021/04/20 12:34)
https://www3.nhk.or.jp/shutoken-news/20210420/1000063263.html
https://malware-log.hatenablog.com/entry/2021/04/20/000000_5
◆サイバー攻撃 中国共産党員の男ら警視庁事情聴取も その後出国 (NHK, 2021/04/20 18:58)
https://www3.nhk.or.jp/news/html/20210420/k10012986251000.html
⇒ https://malware-log.hatenablog.com/entry/2021/04/20/000000_4
◆サイバー攻撃で書類送検に中国反発「証拠示すべき」 (テレ朝, 2021/04/20 19:24)
https://news.tv-asahi.co.jp/news_international/articles/000213592.html
⇒ https://malware-log.hatenablog.com/entry/2021/04/20/000000_6
【ブログ】
■2016年
◆Tick cyberespionage group zeros in on Japan (Symantec, 2016/04/28)
https://www.symantec.com/connect/blogs/tick-cyberespionage-group-zeros-japan
⇒ http://malware-log.hatenablog.com/entry/2016/04/28/000000_4
◆日本を狙い始めたサイバースパイグループ「Tick」 (Symantec, 2016/05/01)
トロイの木馬 Daserf に感染させることを狙って、Web サイトへの侵入とスピア型フィッシングメールが利用されています
http://www.symantec.com/connect/ja/blogs/tick
⇒ http://malware-log.hatenablog.com/entry/2016/05/01/000000
◆APT Daserf (Jul Ismail, 2016/11/29)
APT Campaign Targets Japanese Critical Infrastructure
http://julismail.staff.telkomuniversity.ac.id/apt-daserf/
⇒ http://malware-log.hatenablog.com/entry/2016/11/29/000000
■2017年
◆SHADOWWALI: NEW VARIANT OF THE XXMM FAMILY OF BACKDOORS (CyberReason, 2017/04/25)
https://www.cybereason.com/blog/labs-shadowwali-new-variant-of-the-xxmm-family-of-backdoors
⇒ http://malware-log.hatenablog.com/entry/2018/08/01/212111
◆ビッグデータ時代に昔の手口で検知を逃れるマルウェア (Kaspersky, 2017/05/31)
https://blog.kaspersky.co.jp/old-malware-tricks-to-bypass-detection-in-the-age-of-big-data/15323/
⇒ http://malware-log.hatenablog.com/entry/2017/05/31/000000_5
◆BRONZE BUTLER Targets Japanese Enterprises (SecureWorks, 2017/10/12)
https://www.secureworks.com/research/bronze-butler-targets-japanese-businesses
⇒ http://malware-log.hatenablog.com/entry/2017/10/12/000000_6
◆REDBALDKNIGHT/BRONZE BUTLER’s Daserf Backdoor Now Using Steganography (Trendmicro, 2017/11/07 04:34)
http://blog.trendmicro.com/trendlabs-security-intelligence/redbaldknight-bronze-butler-daserf-backdoor-now-using-steganography/
⇒ http://malware-log.hatenablog.com/entry/2017/11/07/000000_3
◆標的型サイバー攻撃集団「BRONZE BUTLER」によるバックドア型マルウェア「DASERF」、ステガノグラフィを利用 (Trendmicro, 2017/11/14)
http://blog.trendmicro.co.jp/archives/16375
⇒ http://malware-log.hatenablog.com/entry/2017/11/14/000000_5
■2018年
◆日韓両国で展開されるターゲット型攻撃の実態 (Ahnlab, 2018/04/04)
https://jp.ahnlab.com/site/securitycenter/securitycenterboard/securityInsightView.do
⇒ http://malware-log.hatenablog.com/entry/2019/04/04/000000_4
◆Tick Group Weaponized Secure USB Drives to Target Air-Gapped Critical Systems (paloalto, 2018/06/22)
https://unit42.paloaltonetworks.com/unit42-tick-group-weaponized-secure-usb-drives-target-air-gapped-critical-systems/
⇒ https://malware-log.hatenablog.com/entry/2018/06/22/000000_4
◆Tick攻撃グループ、 セキュアUSB ドライブを兵器化し、インターネットから隔離された重要システムを標的に (Paloalto, 2018/06/27)
https://www.paloaltonetworks.jp/company/in-the-news/2018/unit42-tick-group-weaponized-secure-usb-drives-target-air-gapped-critical-systems
⇒ https://malware-log.hatenablog.com/entry/2018/06/27/000000_11
◆Tracking Tick Through Recent Campaigns Targeting East Asia (TALOS, 2018/10/18)
https://blog.talosintelligence.com/2018/10/tracking-tick-through-recent-campaigns.html
⇒ http://malware-log.hatenablog.com/entry/2018/10/18/000000_3
◆東アジアを標的にした最近のキャンペーンを通じて Tick を追跡 (Talos(CISCO), 2018/11/08)
https://gblogs.cisco.com/jp/2018/11/talos-tracking-tick-through-recent-campaigns/
⇒ https://malware-log.hatenablog.com/entry/2018/11/08/000000_6
■2019年
◆Operation ENDTRADE: Finding Multi-Stage Backdoors that TICK (Trendmicro, 2019/11/29 03:29)
https://blog.trendmicro.com/trendlabs-security-intelligence/operation-endtrade-finding-multi-stage-backdoors-that-tick/
⇒ https://malware-log.hatenablog.com/entry/2019/11/29/000000_6
◆ハッカー集団Tickによる日本のシンクタンクや広告代理店を狙った標的型攻撃について (みっきー申す, 2019/12/02)
https://micro-keyword.hatenablog.com/entry/2019/12/02/090704
⇒ https://malware-log.hatenablog.com/entry/2019/12/02/000000_3
◆サイバー攻撃集団「TICK」による「Operation ENDTRADE」 (Trendmicro, 2019/12/12)
https://blog.trendmicro.co.jp/archives/23107
⇒ https://malware-log.hatenablog.com/entry/2019/12/12/000000_11
【公開情報】
■ 2017年
◆日本企業を狙う高度なサイバー攻撃の全貌 – BRONZE BUTLER (SecureWorks, 2017/06/23)
https://www.secureworks.jp/resources/rp-bronze-butler
⇒ https://malware-log.hatenablog.com/entry/2017/06/23/000000_3
◆“Tick” Group Continues Attacks (UNIT42(paloalto), 2017/07/24 18:00)
https://researchcenter.paloaltonetworks.com/2017/07/unit42-tick-group-continues-attacks/
⇒ http://malware-log.hatenablog.com/entry/2017/07/24/000000_2
◆「Tick」グループによる日本や韓国への継続した巧妙な攻撃~ 日本企業の慣習にならい拡張子の変更をお願いする、ソーシャルエンジニアリング的手法を利用 (UNIT42(paloalto), 2017/07/24 18:00)
https://www.paloaltonetworks.jp/company/in-the-news/2017/tick-continues-cyber-espionage-attacks
⇒ http://malware-log.hatenablog.com/entry/2017/07/24/000000_2
◆マルウエアDatperをプロキシログから検知する(2017-08-17) (JPCERT/CC, 2017/08/17)
https://www.jpcert.or.jp/magazine/acreport-datper.html
⇒ http://malware-log.hatenablog.com/entry/2017/08/17/000000_5
■2019年
◆攻撃グループTickによる日本の組織をターゲットにした攻撃活動 (JPCERT/CC, 2019/02/19)
https://blogs.jpcert.or.jp/ja/2019/02/tick-activity.html
⇒ http://malware-log.hatenablog.com/entry/2019/02/19/000000_2
◆攻撃グループ「Tick」が過去10年間に東アジアで行ってきたサイバースパイ活動の実態 (AhnLab(AVAR 2019), 2019/11/07)
https://www.avar2019.org/jp/agenda/day-1/tick-tock-activities-of-the-tick-cyber-espionage-group-in-east-asia-over-the-las-10-years
⇒ https://malware-log.hatenablog.com/entry/2019/11/07/000000_4
■2020年
◆日本の製造業を狙うTickグループ (Macnica Networks, 2020/01/28)
https://www.macnica.net/mpressioncss/feature_05.html/
⇒ https://malware-log.hatenablog.com/entry/2020/01/28/000000_8
【資料】
■2016年
◆CYBER GRID VIEW Vol.2 PDF版 (Lac, 2016/08/02)
http://www.lac.co.jp/security/report/pdf/20160802_cgview_vol2_a001t.pdf
⇒ http://malware-log.hatenablog.com/entry/2016/08/02/000000
■2017年
◆ISTR 22 (Symantec, 2017/04)
https://www.symantec.com/content/dam/symantec/docs/reports/istr-22-2017-en.pdf
⇒ http://malware-log.hatenablog.com/entry/2017/04/30/000000_1
◆日本企業を狙う高度なサイバー攻撃の全貌 – BRONZE BUTLER (SecureWorks, 2017/06/23)
https://www.secureworks.jp/resources/rp-bronze-butler
⇒ https://malware-log.hatenablog.com/entry/2017/06/23/000000_3
◆REDBALDKNIGHT/BRONZE BUTLER’s Daserf Backdoor Now Using Steganography (Trendmicro, 2017/11/07)
https://documents.trendmicro.com/assets/appendix-redbaldknight-bronze-butler-daserf-backdoor-steganography.pdf
⇒ http://malware-log.hatenablog.com/entry/2017/11/07/000000_3
◆JPCERT/CCが見た、標的型攻撃の実態 (久保啓司, 2017/11/28)
https://www.nic.ad.jp/ja/materials/iw/2017/proceedings/d1/d1-1-kubo.pdf
⇒ http://malware-log.hatenablog.com/entry/2017/11/28/000000_7
■2018年
◆日本を狙うサイバーエスピオナージ (標的型攻撃)の動向 2018 年上半期 (Macnica Networks, 2018/10/01)
https://www.macnica.net/file/mpressioncss_2018-1h-report_mnc_rev3_nopw.pdf
■2019年
◆Tick グループの最新攻撃事例分析 (Ahmlab, 2019/04/22)
https://jp.ahnlab.com/global/upload/download/asecreport/PressAhn_Vol64.pdf
⇒ https://malware-log.hatenablog.com/entry/2019/04/22/000000_5
◆Tick Tock - Activities of hte Tick Cyber Espionage Group in EastAsia Over the last 10 Years (AhnLab, 2019/11/26)
https://www.slideshare.net/JackyMinseokCha/tick-group-avar2019-20191111-cha-minseokpublish
⇒ https://malware-log.hatenablog.com/entry/2019/11/26/000000_4
◆Operation ENDTRADE: TICK’s Multi-Stage Backdoors for Attacking Industries and Stealing Classified Data (Trendmicro, 2019/11/29)
https://documents.trendmicro.com/assets/pdf/Operation-ENDTRADE-Tick-Multi-Stage-Backdoors-for-Attacking-Industries-and-Stealing-Classified-Data.pdf
⇒ https://malware-log.hatenablog.com/entry/2019/11/29/000000_7
◆標的型攻撃の実態と対策アプローチ 第4版 (Macnica Networks, 2020/05/26)
https://www.macnica.net/mpressioncss/feature_06.html/
⇒ https://malware-log.hatenablog.com/entry/2020/05/26/000000_4
【IoC情報】
◆Daserf (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000
◆HomamDownloader (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_1
◆Custom Gh0st (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_2
◆Gh0stRAt Downloader (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_3
◆NamelessHdoor (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_4
◆Minzen (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_5
◆9002 (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_6
◆Invader (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_7
◆Datper (IoC (TT Malware Log), 2017/07/24)
https://ioc.hatenablog.com/entry/2017/07/24/000000_8
◆Datper (IoC (TT Malware Log))
https://ioc.hatenablog.com/entry/2017/08/17/000000
◆MSGet downloader (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000
◆VBE downloader (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_1
◆Daserf(Visual C) (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_2
◆Daserf(Delphi) (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_3
◆Datper (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_4
◆xxmm (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_5
◆xxmm downloader (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_6
◆DGet (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_7
◆RarStar (IoC (TT Malware Log), 2017/10/12)
https://ioc.hatenablog.com/entry/2017/10/12/000000_8
◆Tick (IoC (TT Malware Log), 2019/02/19)
https://ioc.hatenablog.com/entry/2019/02/19/000000
◆Tick (IoC (TT Malware Log), 2019/02/22)
https://ioc.hatenablog.com/entry/2019/02/22/000000
◆Tick (IoC (TT Malware Log), 2019/11/29)
https://ioc.hatenablog.com/entry/2019/11/29/000000
【図表】



出典: https://internet.watch.impress.co.jp/docs/news/1099223.html

BRONZE BUTLERが使うマルウェアの変遷(出典:Secureworks)
出典: http://www.itmedia.co.jp/enterprise/articles/1710/16/news050.html

「[wali]」セクションの文字列

「wali.exe」のファイル名
出典: https://blog.kaspersky.co.jp/old-malware-tricks-to-bypass-detection-in-the-age-of-big-data/15323/

出典: http://scan.netsecurity.ne.jp/article/img/2016/08/03/38799/20656.html
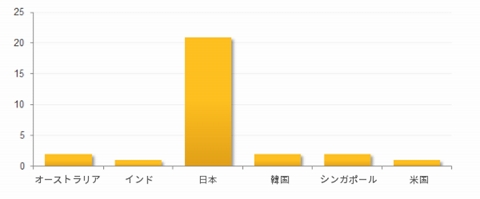
出典: https://internet.watch.impress.co.jp/docs/news/756214.html

最近の日本に対する攻撃で見つかった感染チェーン

地域別の Daserf 感染数
出典: https://www.symantec.com/connect/nl/blogs/tick?page=1

出典: https://www.symantec.com/connect/blogs/tick-cyberespionage-group-zeros-japan

出典: https://jp.ahnlab.com/site/securitycenter/securitycenterboard/securityInsightView.do

全国政治協商会議からみる中国動向(資料出典:サイント)

日本から見た脅威アクターの連携の可能性(資料出典:サイント)

サイントが観測した2018年以降の戦略支援部隊の標的分野(資料出典:サイント)
出典: https://enterprisezine.jp/article/detail/12300

「エンドトレード作戦」で利用されたマルウェア

巧みな日本語で書かれた標的型メールの例
出典: https://blog.trendmicro.co.jp/archives/23107

出典: https://www.macnica.net/mpressioncss/feature_05.html/

2018年、2019年に攻撃を観測した業種

配送されたファイル

Tickの活動タイムライン

攻撃フロー
出典: https://www.macnica.net/mpressioncss/feature_05.html/
| 時期 | 対象 | 攻撃手法 |
|---|---|---|
| 2013年2月 | 不明 | Flash 脆弱性(CVE-2013-0633、CVE-2013-0634)を利用した攻撃 |
| 2014年3月 | 韓国 - 防衛産業 | Netboy 変形で攻撃。韓国で多数の感染報告 |
| 2015年1月 | 韓国 - 大企業 A | Bisodown 変形で攻撃 |
| 2015年5月 | 韓国 - 大企業 B | Netboy 変形で攻撃 |
| 2015年6月 | アジア - 金融機関 | 確認不可 |
| 2016年2月 | 韓国 - 海洋産業 | Daserf 変形で攻撃。2016年6月、韓国のキャリアで発見された Daserfマルウェアと同じ |
| 2016年6月 | 日本 - 旅行会社 | LAC レポートによる |
| 2016年6月 | 韓国 - キャリア | Daserf 変形で攻撃 |
| 2016年9月 | 韓国 - エネルギー | Datper 変形で攻撃 |
| 2016年12月 | 日本 - 企業 | 日本の資産管理ソフトウェアの脆弱性(CVE-2016-7836)を攻撃して感染 |
| 2017年4月 | 韓国 - 未確認 | 2018年パロアルトユニット42を通じて韓国のセキュアUSBへの攻撃が知られた |
| 2018年5月 | 韓国 - 国防分野推定 | Bisodown 変形で攻撃。軍事関連内容に偽装したファイル(decoy)などからみて国防分野の関係者がターゲットと推定される |
| 2018年5月 | 韓国 - 政治機関 | Bisodown 利用攻撃 |
| 2018年8月 | 韓国 - 国防分野 | Bisodown 変形で攻撃。感染システムで Linkinfo.dllファイル名を持つ Keyloggerと一緒に発見 |
| 2018年9月 | 韓国 - 政治機関 | Datper 変形で攻撃 |
| 2019年1月 | 韓国 - 情報セキュリティ | JPCERT で 2019年2月に公開した Datper 変形で攻撃 |
| 2019年1月 | 韓国 - Webホスティング | 2019年1月、韓国のセキュリティベンダーで発見されたマルウェアと同じ |
| 2019年2月 | 韓国 - 電子部品 | JPCERTで2019年2月に公開した Datper 変形で攻撃 |
| 2019年2月 | 韓国-ITサービス | 2019年2月、韓国の電子部品の攻撃マルウェアと同じ Datper 変形で攻撃 |
【関連情報】
◆Lilith (werkamsus, 2019/09/19)
https://malware-log.hatenablog.com/entry/2019/11/29/000000_14
関連情報
【関連まとめ記事】
◆標的型攻撃組織 / APT (まとめ)
https://malware-log.hatenablog.com/entry/APT
◆Daserf (まとめ)
http://malware-log.hatenablog.com/entry/Daserf
◆Datper (まとめ)
http://malware-log.hatenablog.com/entry/Datper
【攻撃手法】
【セキュアUSBドライブ】
◆Tick Group Weaponized Secure USB Drives to Target Air-Gapped Critical Systems (paloalto, 2018/06/22)
https://unit42.paloaltonetworks.com/unit42-tick-group-weaponized-secure-usb-drives-target-air-gapped-critical-systems/
⇒ https://malware-log.hatenablog.com/entry/2018/06/22/000000_4
◆攻撃グループ「Tick」、資産管理ソフトへの脆弱性攻撃を継続 - 標的型攻撃も (Security NEXT, 2019/02/22)
http://www.security-next.com/102741
⇒ http://malware-log.hatenablog.com/entry/2019/02/22/000000_1
◆Tick攻撃グループ、 セキュアUSB ドライブを兵器化し、インターネットから隔離された重要システムを標的に (Paloalto, 2018/06/27)
https://www.paloaltonetworks.jp/company/in-the-news/2018/unit42-tick-group-weaponized-secure-usb-drives-target-air-gapped-critical-systems
⇒ https://malware-log.hatenablog.com/entry/2018/06/27/000000_11
◆Tick APTハッキンググループ、韓国の防衛産業が作成したセキュリティUSBターゲットに攻撃 (Dailysecu, 2018/06/27 22:07)
https://www.dailysecu.com/news/articleView.html?idxno=35901
⇒ https://malware-log.hatenablog.com/entry/2018/06/27/000000_10