【図表】

出典: https://www.zdnet.com/article/us-charges-five-hackers-part-of-chinese-state-sponsored-group-apt41/
【目次】
概要
【別名】
| 攻撃組織名 | 命名組織 |
|---|---|
| Winnti | 一般的 (Kaspersky, ESET, Cleasky) |
| APT41 | FireEye |
| Blackfly | |
| Suckfly | Symantec |
| Wicked Panda | |
| Wicked Spider | |
| Barium | Microsoft |
| Amoeva | TeamT5 |
| Bronze Atlas | Dell Secure Works |
| UNIT2025 | |
| MISSION2025 |
【辞書】
■組織
◆Group: Winnti Group, Blackfly (ATT&CK)
https://attack.mitre.org/wiki/Group/G0044
◆Suckfly APT (IBM X-Force Exchange)
https://exchange.xforce.ibmcloud.com/collection/Suckfly-APT-aa8af56fd12d25c98fc49ca5341160ab
◆Axiom (ATT&CK)
https://attack.mitre.org/groups/G0001/
◆Winnti (Malpedia)
https://malpedia.caad.fkie.fraunhofer.de/details/win.winnti
◆Winnti Umbrella
https://malpedia.caad.fkie.fraunhofer.de/actor/winnti_umbrella
■マルウェア
◆Winnti (NJCCIC)
https://www.cyber.nj.gov/threat-profiles/trojan-variants/winnti
【概要】
| 項目 | 内容 |
|---|---|
| 活動時期 | 2009~(Kaspersky), 2010~(?) |
| 活動場所 | 成都(Symantec) |
| 使用マルウェア | Winnti, Nidiran |
| 攻撃対象 | オンラインゲーム企業 |
| 攻撃の目的 | オンラインゲームのソースコードを含む知的財産の盗難 |
| 正規のソフトウェアベンダーによって署名されたデジタル証明書の獲得 | |
| 関連組織 | APT17, Ke3chang, Axiom |
| 攻撃対象国 | 韓国、ドイツ、米国、日本、中国、ロシア、ブラジル、ペルー、ベラルーシ |
| 攻撃対象企業 | ネクソン(日本) |
| 収益化スキーム | 産業スパイ |
| ゲーム内の仮想通貨を現実の通貨に変えるリアルマネートレード(RMT) | |
| 海賊版サーバの展開 |
■キャンペーン名
| キャンペーン名 | 命名組織 |
|---|---|
| Vision2025 |
■攻撃対象国
| 対象国名 |
|---|
| オーストラリア |
| カナダ |
| デンマーク |
| フィンランド |
| フランス |
| インド |
| イタリア |
| 日本 |
| マレーシア |
| メキシコ |
| フィリピン |
| ポーランド |
| カタール |
| サウジアラビア |
| シンガポール |
| スウェーデン |
| スイス |
| UAE |
| 英国 |
| 米国 |
■関連組織
| 関連組織 | 備考 |
|---|---|
| (Axiom) | Winnti と同じマルウェアを使用 |
| (Group 72) |
■使用マルウェア
| マルウェア名 | 備考 |
|---|---|
| Winnti | |
| Highnoon | |
| PipeMon |
【最新情報】
◆Winnti's new UNAPIMON tool hides malware from security software (BleepingComputer, 2024/04/02 17:59)
[Winntiの新ツール「UNAPIMON」、セキュリティ・ソフトウェアからマルウェアを隠す]
https://www.bleepingcomputer.com/news/security/winntis-new-unapimon-tool-hides-malware-from-security-software/
⇒ https://malware-log.hatenablog.com/entry/2024/04/02/000000_3
記事
【ニュース】
■2013年
◆Priority Intelligence Report: WINNTI Group Changing Targets (The Register, 2013/04/11)
http://www.theregister.co.uk/2013/04/11/video_game_cyberespionage/
⇒ http://malware-log.hatenablog.com/entry/2013/04/11/000000_2
◆サイバー犯罪組織「Winnti」、ゲーム制作会社を標的に……カスペルスキーが報告書公開 (RBB Today, 2013/04/12 13:26)
https://www.rbbtoday.com/article/2013/04/12/106262.html
⇒ http://malware-log.hatenablog.com/entry/2013/04/12/000000_2
◆世界のオンラインゲーム会社を標的とするサイバースパイ活動を分析--Kaspersky (ZDNet, 2013/04/12 15:30)
https://japan.zdnet.com/article/35030780/
⇒ http://malware-log.hatenablog.com/entry/2013/04/12/000000_2
◆ハッカー集団のWinnti、4年にわたりオンラインゲーム開発会社へサイバー攻撃 (ビジネス+IT, 2013/04/12)
http://www.sbbit.jp/article/cont1/26189
⇒ https://malware-log.hatenablog.com/entry/2013/04/12/000000_5
◆Backdoor Built With Aheadlib Used In Targeted Attacks? (Trendmicro, 2013/05/09)
http://blog.trendmicro.com/trendlabs-security-intelligence/backdoor-built-with-aheadlib-used-in-targeted-attacks/
⇒ http://malware-log.hatenablog.com/entry/2013/05/09/000000_1
◆ゲーム会社への標的攻撃に使用された「WINNTI」ファミリ類似の亜種を確認 (Trendmicro, 2013/05/17)
http://blog.trendmicro.co.jp/archives/7252
⇒ http://malware-log.hatenablog.com/entry/2013/05/17/000000_1
■2015年
◆Winnti trojan may help set stage for Skeleton Key attacks, analysts say (SC Media, 2015/01/29)
https://www.scmagazine.com/home/security-news/winnti-trojan-may-help-set-stage-for-skeleton-key-attacks-analysts-say/
⇒ https://malware-log.hatenablog.com/entry/2015/01/29/000000_1
◆Winnti Malware Gets into Pharmaceutical Business (Softpedia, 2015/06/23)
https://news.softpedia.com/news/winnti-malware-gets-into-pharmaceutical-business-485013.shtml
⇒ https://malware-log.hatenablog.com/entry/2015/06/23/000000_2
◆「MERS予防」装う標的型攻撃、「CHMファイル」に注意 (Security NEXT, 2015/06/30)
http://www.security-next.com/060001/2
⇒ https://malware-log.hatenablog.com/entry/2015/06/30/000000_1
■2016年
◆'Suckfly' in the ointment: Chinese APT group steals code-signing certificates (SC Magazine, 2016/03/16)
https://www.scmagazine.com/suckfly-in-the-ointment-chinese-apt-group-steals-code-signing-certificates/article/528968/
⇒ http://malware-log.hatenablog.com/entry/2016/03/16/000000_3
◆Suckfly: Revealing the secret life of your code signing certificates (Symantec, 2016/05/15)
https://www.symantec.com/connect/blogs/suckfly-revealing-secret-life-your-code-signing-certificates
⇒ https://malware-log.hatenablog.com/entry/2016/05/15/000000
◆Indian organizations targeted in Suckfly attacks (Symantec, 2016/05/17)
https://www.symantec.com/connect/blogs/indian-organizations-targeted-suckfly-attacks
⇒ https://malware-log.hatenablog.com/entry/2016/05/17/000000_3
◆Suckfly Cyber-Espionage Group Targets Indian Government and Private Companies (Softpedia, 2016/05/18)
http://news.softpedia.com/news/suckfly-cyber-espionage-group-targets-indian-government-and-private-companies-504183.shtml
⇒ https://malware-log.hatenablog.com/entry/2016/05/18/000000_3
◆Suckfly APT (XForce, 2016/06/03)
https://exchange.xforce.ibmcloud.com/collection/Suckfly-APT-aa8af56fd12d25c98fc49ca5341160ab
⇒ https://malware-log.hatenablog.com/entry/2016/06/03/000000_4
◆'Suckfly' in the ointment: Chinese APT group steals code-signing certificates (SC Magazine, 2016/03/16)
https://www.scmagazine.com/suckfly-in-the-ointment-chinese-apt-group-steals-code-signing-certificates/article/528968/
⇒ https://malware-log.hatenablog.com/entry/2016/03/16/000000_3
◆Suckfly Cyber-Espionage Group Targets Indian Government and Private Companies (Softpedia, 2016/05/18)
http://news.softpedia.com/news/suckfly-cyber-espionage-group-targets-indian-government-and-private-companies-504183.shtml
⇒ https://malware-log.hatenablog.com/entry/2016/05/18/000000_3
◆Indian organizations targeted in Suckfly attacks (Symantec, 2016/05/17)
https://www.symantec.com/connect/blogs/indian-organizations-targeted-suckfly-attacks
⇒ https://malware-log.hatenablog.com/entry/2016/05/17/000000_3
◆インドの組織を狙う Suckfly (Symantec, 2016/05/19)
https://www.symantec.com/connect/nl/blogs/suckfly-2?page=1
⇒ http://malware-log.hatenablog.com/entry/2016/05/19/000000_3
■2017年
◆Research claims CCLeaner attack carried out by Chinese-linked group (CyberScoop, 2017/10/02)
https://www.cyberscoop.com/ccleaner-attack-china-intezer-labs-piriform-apt17/
⇒ https://malware-log.hatenablog.com/entry/2017/10/02/000000_4
■2019年
◆Bayer contains cyber attack it says bore Chinese hallmarks (ロイター, 2019/04/04 16:35)
https://www.reuters.com/article/us-bayer-cyber/bayer-says-has-detected-contained-cyber-attack-idUSKCN1RG0NN
⇒ http://malware-log.hatenablog.com/entry/2019/04/04/000000
◆ドイツの大手製薬会社バイエルにサイバー攻撃、「データ窃盗が行われた形跡はなし」 (ZDNet, 2019/04/05 11:26)
https://japan.zdnet.com/article/35135308/
⇒ http://malware-log.hatenablog.com/entry/2019/04/05/000000_2
◆Barium Group Using Backdoors in Trusted Software to Wage Supply Chain Attacks (SecurityIntelligence, 2019/05/08 11:55)
https://securityintelligence.com/news/barium-group-using-backdoors-in-trusted-software-to-wage-supply-chain-attacks/
⇒ https://malware-log.hatenablog.com/entry/2019/05/08/000000_12
◆中国政府支援のハッカー集団、仮想通貨取引所やゲーム企業をターゲットに=セキュリティ企業がレポート (CoinTelegraph, 2019/08/08)
https://jp.cointelegraph.com/news/chinese-govt-hackers-are-targeting-crypto-companies-report
⇒ https://malware-log.hatenablog.com/entry/2019/08/08/000000_6
◆中国政府が支援するハッカー集団を特定か、暗号通貨やゲーム業界が対象 (The Nodist, 2019/08/09)
https://jp.thenodist.com/articles/12094
⇒ https://malware-log.hatenablog.com/entry/2019/08/09/000000_1
◆中国のサイバー攻撃集団が、7年にわたり世界の医療データを攻撃していた (NewsWeek, 2019/08/26 19:45)
https://www.newsweekjapan.jp/stories/world/2019/08/post-12849.php
⇒ https://malware-log.hatenablog.com/entry/2019/08/26/000000_7
◆中国のハッカー、がん研究機関を標的に--FireEye報告書 (ZDNet, 2019/08/27 07:30)
https://japan.zdnet.com/article/35141754/
⇒ https://malware-log.hatenablog.com/entry/2019/08/27/000000
◆Beyond Compliance:Cyber Threats and Healthcare (FireEye, 2019/08/27)
https://content.fireeye.com/cyber-security-for-healthcare/rpt-beyond-compliance-cyber-threats-and-healthcare
⇒ https://malware-log.hatenablog.com/entry/2019/08/27/000000_6
◆PC遠隔操作ソフト「TeamViewer」を利用したシステムにサイバー攻撃グループがアクセス可能であるとの指摘、中国のセキュリティ企業は否定 (Gigazine, 2019/10/21 15:30)
https://gigazine.net/news/20191021-apt41-teamviewer/
⇒ https://malware-log.hatenablog.com/entry/2019/10/21/000000
◆APT 41 using MessageTap malware to gather SMS traffic (SC Media, 2019/11/01)
https://www.scmagazineuk.com/apt-41-using-messagetap-malware-gather-sms-traffic/article/1664452
⇒ https://malware-log.hatenablog.com/entry/2019/11/01/000000_5
◆サイバー犯罪者組織Winnti Groupの手口を紹介 (ASCII.jp, 2019/11/21 14:00)
https://ascii.jp/elem/000/001/978/1978116/
⇒ https://malware-log.hatenablog.com/entry/2019/11/21/000000
■2020年
◆Winnti Group、香港の大学に対して新たな攻撃を実行 (ASCII.jp, 2020/03/04 14:00)
https://ascii.jp/elem/000/004/004/4004690/
⇒ https://malware-log.hatenablog.com/entry/2020/03/04/000000_2
◆米国のサイバーセキュリティ専門家、中国のデジタルスパイ活動の最近の急増を確認 (ラベルオンライン, 2020/03/25)
https://label-online.jp/%E7%B1%B3%E5%9B%BD%E3%81%AE%E3%82%B5%E3%82%A4%E3%83%90%E3%83%BC%E3%82%BB%E3%82%AD%E3%83%A5%E3%83%AA%E3%83%86%E3%82%A3%E5%B0%82%E9%96%80%E5%AE%B6%E3%80%81%E4%B8%AD%E5%9B%BD%E3%81%AE%E3%83%87%E3%82%B8/
⇒ https://malware-log.hatenablog.com/entry/2020/03/25/000000_1
◆Chinese Hackers Exploit Cisco, Citrix Flaws in Massive Espionage Campaign (Threat Post, 2020/03/25)
Researchers say that APT41’s exploits are part of one of the broadest espionage campaigns they’ve seen from a Chinese-linked actor “in recent years.”
(研究者によると、APT41のエクスプロイトは、「近年」中国に関連するActorから見た最も広範なスパイ活動の1つであるとのことです)https://threatpost.com/chinese-hackers-exploit-cisco-citrix-espionage/154133/
⇒ https://malware-log.hatenablog.com/entry/2020/03/25/000000_2
◆CitrixやZohoの脆弱性を突く大規模攻撃が発生中 (ITmedia, 2020/03/26 10:38)
FireEyeによると、中国のサイバースパイ集団「APT41」がCitrixやCisco、Zohoの製品の脆弱性を突いて、世界各地で大規模攻撃を仕掛けている
https://www.itmedia.co.jp/enterprise/articles/2003/26/news072.html
⇒ https://malware-log.hatenablog.com/entry/2020/03/26/000000_1
◆APT41 Distributing Speculoos Backdoor in New Attack Campaign (Security Intelligence, 2020/04/15 14:30)
https://securityintelligence.com/news/apt41-distributing-speculoos-backdoor-in-new-attack-campaign/
⇒ https://malware-log.hatenablog.com/entry/2020/04/15/000000_4
◆中国ハッカーに握られた社内PC 特命チーム暗闘の全貌 (朝日新聞, 2020/05/08 07:00)
https://digital.asahi.com/articles/ASN544T17N52ULZU00F.html
⇒ https://malware-log.hatenablog.com/entry/2020/05/08/000000_1
◆Chinese Hackers Have Pillaged Taiwan's Semiconductor Industry (WIRED, 2020/08/06 17:38)
[中国のハッカーは、台湾の半導体産業を脅かした]A campaign called Operation Skeleton Key has stolen source code, software development kits, chip designs, and more.
[Operation Skeleton Key というキャンペーンで、ソースコードやソフトウェア開発キット、チップデザインなどが盗まれています。]https://www.wired.com/story/chinese-hackers-taiwan-semiconductor-industry-skeleton-key/
⇒ https://malware-log.hatenablog.com/entry/2020/08/06/000000_4
◆Chinese hackers have pillaged Taiwan’s semiconductor industry (Ars Technica, 2020/08/09 19:56)
[中国のハッカーは台湾の半導体産業を略奪した]Operation Skeleton Key has stolen source code, SDKs, chip designs, and more.
[Operation Skeleton Keyは、ソースコード、SDK、チップデザインなどを盗み出しています。]https://arstechnica.com/information-technology/2020/08/chinese-hackers-have-pillaged-taiwans-semiconductor-industry/
⇒ https://malware-log.hatenablog.com/entry/2020/08/09/000000_2
◆中国政府系ハッカーが台湾の半導体産業から戦略的に情報を盗み出している証拠とは? (Gigazine, 2020/08/12 06:00)
https://gigazine.net/news/20200812-chinese-hackers-taiwans-semiconductor-industry/
⇒ https://malware-log.hatenablog.com/entry/2020/08/12/000000_1
◆US charges five hackers part of Chinese state-sponsored group APT41 (ZDNet, 2020/09/16 15:03)
[米国は5人のハッカーを告発する 中国の国営グループAPT41の一部である]US says APT41 orchestrated intrusions at more than 100 companies across the world, ranging from software vendors, video gaming companies, telcos, and more.
[米国によると、APT41は、ソフトウェアベンダー、ビデオゲーム会社、通信事業者など、世界中の100社以上の企業への侵入を指揮したという。]https://www.zdnet.com/article/us-charges-five-hackers-part-of-chinese-state-sponsored-group-apt41/
⇒ https://malware-log.hatenablog.com/entry/2020/09/16/000000
◆米検察、サイバー攻撃で中国人を訴追 100社超を標的 (WSJ, 2020/09/17)
https://jp.wsj.com/articles/SB11303078305990274332104586635913401934734
⇒ https://malware-log.hatenablog.com/entry/2020/09/17/000000
■2021年
◆China's APT hackers move to ransomware attacks (BleepingComputer, 2021/01/04 09:36)
[中国のAPTハッカーがランサムウェア攻撃に動く]
https://www.bleepingcomputer.com/news/security/chinas-apt-hackers-move-to-ransomware-attacks/
⇒ https://malware-log.hatenablog.com/entry/2021/01/04/000000
◆Microsoft社のデジタル署名を悪用した「Cobalt Strike loader」による標的型攻撃〜攻撃者グループAPT41 (Lac, 2021/05/21)
https://www.lac.co.jp/lacwatch/report/20210521_002618.html
⇒ https://malware-log.hatenablog.com/entry/2021/05/21/000000_8
◆Monumental Supply-Chain Attack on Airlines Traced to State Actor (ThreatPost, 2021/06/11 10:23)
https://threatpost.com/supply-chain-attack-airlines-state-actor/166842/
⇒ https://malware-log.hatenablog.com/entry/2021/06/11/000000_15
◆中国当局支援のハッカー集団、個体情報管理するインド政府機関などに不正侵入=米調査 (大紀元, 2021/09/25 11:40)
https://www.epochtimes.jp/p/2021/09/79372.html
⇒ https://malware-log.hatenablog.com/entry/2021/09/25/000000_3
■2022年
◇2022年3月
◆家畜の管理システムを狙って州政府のネットワークに侵入、中国のハッカー集団による巧妙な手口 (Wired, 2022/03/18)
https://wired.jp/article/china-apt41-hacking-usaherds-log4j/
⇒ https://malware-log.hatenablog.com/entry/2022/03/18/000000_11
◆Chinese hacking group uses new 'Fire Chili' Windows rootkit (BleepingComputer, 2022/03/31)
[中国のハッカー集団が新しい「Fire Chili」Windows rootkitを使用]
https://www.bleepingcomputer.com/news/security/chinese-hacking-group-uses-new-fire-chili-windows-rootkit/
⇒ https://malware-log.hatenablog.com/entry/2022/03/31/000000_4
◇2022年4月
◆中国のハッカー集団APT41が、米国の家畜管理システムに謎の攻撃 (Forbes, 2022/04/30 07:00)
https://forbesjapan.com/articles/detail/47238
⇒ https://malware-log.hatenablog.com/entry/2022/04/30/000000
◇2022年8月
◆Winnti hackers split Cobalt Strike into 154 pieces to evade detecti (BleepingComputer, 2022/08/18 11:48)
[WinntiのハッカーはCobalt Strikeを154個に分割して検知を回避]
https://www.bleepingcomputer.com/news/security/winnti-hackers-split-cobalt-strike-into-154-pieces-to-evade-detection/
⇒ https://malware-log.hatenablog.com/entry/2022/08/18/000000_1
◆China-backed APT41 Hackers Targeted 13 Organisations Worldwide Last Year (The Hacker News, 2022/08/18)
https://thehackernews.com/2022/08/china-backed-apt41-hackers-targeted-13.html
⇒ https://malware-log.hatenablog.com/entry/2022/08/18/000000_6
◆中国の攻撃グループ「APT41」、2021年に少なくとも世界の13組織を攻撃 (マイナビニュース, 2022/08/23 08:32)
https://news.mynavi.jp/techplus/article/20220823-2431769/
⇒ https://malware-log.hatenablog.com/entry/2022/08/23/000000
◇2022年12月
◆中国ハッカー集団、米コロナ救済資金数千万ドルを盗難=当局 (ロイター, 2022/12/06 04:29)
https://jp.reuters.com/article/cyber-china-covid-idJPL6N32V0CE
⇒ https://malware-log.hatenablog.com/entry/2022/12/06/000000_1
◆中国系ハッカーが新型コロナ給付金27億円超を盗み出したことが判明 (Gigazine, 2022/12/06)
https://gigazine.net/news/20221206-chinese-hacker-steals-covid-benefits/
⇒ https://malware-log.hatenablog.com/entry/2022/12/06/000000
■2023年
◇2023年2月
◆中国のサイバースパイ集団、新たに南米の外交機関を標的に (CIO, 2023/02/17)
https://project.nikkeibp.co.jp/idg/atcl/19/00002/00437/
⇒ https://malware-log.hatenablog.com/entry/2023/02/17/000000_3
◇2023年3月
◆New Mélofée Linux malware linked to Chinese APT groups (SecurityAffairs, 2023/03/30)
[中国のAPTグループと連携した新しいMélofée Linuxマルウェア]
https://securityaffairs.com/144210/apt/melofee-malware-linked-to-china.html
⇒ https://malware-log.hatenablog.com/entry/2023/03/30/000000_4
■2023年
◇2024年4月
◆Winnti's new UNAPIMON tool hides malware from security software (BleepingComputer, 2024/04/02 17:59)
[Winntiの新ツール「UNAPIMON」、セキュリティ・ソフトウェアからマルウェアを隠す]
https://www.bleepingcomputer.com/news/security/winntis-new-unapimon-tool-hides-malware-from-security-software/
⇒ https://malware-log.hatenablog.com/entry/2024/04/02/000000_3
【ブログ】
■2013年
◆Winnti 1.0 technical analysis (SECURELIST, 2013/04/11)
https://securelist.com/winnti-1-0-technical-analysis/37002/
⇒ http://malware-log.hatenablog.com/entry/2013/04/11/000000_7
◆The Winnti honeypot – luring intruders (SECURELIST, 2013/04/11)
https://securelist.com/the-winnti-honeypot-luring-intruders/35623/
⇒ http://malware-log.hatenablog.com/entry/2013/04/11/000000_3
◆Winnti-Stolen Digital Certificates Re-Used in Current Watering Hole Attacks on Tibetan and Uyghur Groups (SECURELIST, 2013/04/12)
https://securelist.com/winnti-stolen-digital-certificates-re-used-in-current-watering-hole-attacks-on-tibetan-and-uyghur-groups-3/35692/
⇒ http://malware-log.hatenablog.com/entry/2013/04/12/000000_4
◆Winnti returns with PlugX (SECURELIST, 2013/04/15 12:30 GMT)
http://www.securelist.com/en/blog/208194224/Winnti_returns_with_PlugX
⇒ http://malware-log.hatenablog.com/entry/2013/04/15/000000_1
◆Backdoor Built With Aheadlib Used In Targeted Attacks? (Trendmicro, 2013/05/09)
http://blog.trendmicro.com/trendlabs-security-intelligence/backdoor-built-with-aheadlib-used-in-targeted-attacks/
⇒ http://malware-log.hatenablog.com/entry/2013/05/09/000000_1
■2015年
◆Games are over: Winnti is now targeting pharmaceutical companies (Kaspersky, 2015/06/22 14:19)
https://securelist.com/games-are-over/70991/
⇒ https://malware-log.hatenablog.com/entry/2015/06/22/000000_2
◆I am HDRoot! Part 1 (SECURE LIST, 2015/10/06)
https://securelist.com/i-am-hdroot-part-1/72275/
⇒ https://malware-log.hatenablog.com/entry/2015/10/06/000000
■2016年
◆PlugX malware: A good hacker is an apologetic hacker (SecureList, 2016/03/10 11:59)
https://securelist.com/blog/virus-watch/74150/plugx-malware-a-good-hacker-is-an-apologetic-hacker/
⇒ https://malware-log.hatenablog.com/entry/2016/03/10/000000_3
◆Suckfly: Revealing the secret life of your code signing certificates (Symnatec, 2016/03/15)
https://www.symantec.com/connect/blogs/suckfly-revealing-secret-life-your-code-signing-certificates
⇒ https://malware-log.hatenablog.com/entry/2016/03/15/000000_6
◆インドの組織を狙う Suckfly (Symantec, 2016/05/18)
Suckfly が、インドの政府機関と営利企業を標的にして、長期にわたるスパイ活動を展開しています。
https://www.symantec.com/connect/blogs/suckfly-2
⇒ http://malware-log.hatenablog.com/entry/2016/05/18/000000_4
◆インドの組織を狙う Suckfly (Symantec, 2016/05/19)
https://www.symantec.com/connect/nl/blogs/suckfly-2?page=1
⇒ http://malware-log.hatenablog.com/entry/2016/05/19/000000_3
◆Suckfly (Schneier on Security, 2016/05/26 06:31)
https://www.schneier.com/blog/archives/2016/05/suckfly.html
⇒ https://malware-log.hatenablog.com/entry/2016/05/26/000000_5
■2017年
◆「WINNTI」、C&C通信にGitHubを悪用 (Trendmicro, 2017/03/30)
http://blog.trendmicro.co.jp/archives/14654
⇒ https://malware-log.hatenablog.com/entry/2017/03/30/000000
◆Of Pigs and Malware: Examining a Possible Member of the Winnti Group (Trendmicro, 2017/04/19)
https://blog.trendmicro.co.jp/archives/14794
⇒ https://malware-log.hatenablog.com/entry/2018/07/16/114802
◆サイバー犯罪者集団「WINNTI」に関与するメンバーを特定か (Trendmicro, 2017/04/27)
http://blog.trendmicro.co.jp/archives/14794
⇒ http://malware-log.hatenablog.com/entry/2017/04/27/000000_2
■2018年
◆Meet CrowdStrike’s Adversary of the Month for July: WICKED SPIDER (CroudStrike, 2018/07/26)
https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-july-wicked-spider/
⇒ http://malware-log.hatenablog.com/entry/2018/07/26/000000_8
■2019年
◆APT41:スパイ活動とサイバー犯罪の両方を遂行する双頭龍の攻撃者 (FireEye, 2019/08/08)
https://www.fireeye.jp/blog/jp-threat-research/2019/08/apt41-dual-espionage-and-cyber-crime-operation.html
⇒ https://malware-log.hatenablog.com/entry/2019/08/08/000000_7
◆GAME OVER: Detecting and Stopping an APT41 Operation (FireEye, 2019/08/19)
https://www.fireeye.com/blog/threat-research/2019/08/game-over-detecting-and-stopping-an-apt41-operation.html
⇒ https://malware-log.hatenablog.com/entry/2019/08/19/000000_8
◆Winnti Group’s skip‑2.0: A Microsoft SQL Server backdoor (WeLiveSecurity, 2019/10/21 11:30)
Notorious cyberespionage group debases MSSQL
https://www.welivesecurity.com/2019/10/21/winnti-group-skip2-0-microsoft-sql-server-backdoor/
⇒ https://malware-log.hatenablog.com/entry/2019/10/21/000000_7
■2020年
◆Winnti Groupが香港の大学に仕掛けた新たな攻撃 (キヤノンマーケティングジャパン, 2020/03/04)
https://eset-info.canon-its.jp/malware_info/trend/detail/200304.html
⇒ https://malware-log.hatenablog.com/entry/2020/03/04/000000_2
◆Red Wall-Stone Panda-Highnoon-MISSION2025-Winnti-APT41-VISION 2025 Are YOU Being Targeted By China? (PSBE, 2020/04/07)
https://www.cybernewsgroup.co.uk/red-wall-stone-panda-highnoon-mission2025-winnti-apt41-vision-2025-are-you-being-targeted-by-chinas-vision-2025-campaign-do-not-become-a-victim-of-a-malign-chinese-mission/
⇒ https://malware-log.hatenablog.com/entry/2020/04/07/000000_2
◆WINNTI GROUP: Insights From the Past (Quointelligence, 2020/04/20)
https://quointelligence.eu/2020/04/winnti-group-insights-from-the-past/
⇒ https://malware-log.hatenablog.com/entry/2020/04/20/000000_4
◆Taiwan suggests China’s Winnti group is behind ransomware attack on state oil company (CyberScoop, 2020/05/18)
台湾は中国のWinntiグループが国営石油会社へのランサムウェア攻撃の背後にあることを示唆
https://www.cyberscoop.com/cpc-ransomware-winnti-taiwan-china/
⇒ https://malware-log.hatenablog.com/entry/2020/05/18/000000_3
◆No “Game over” for the Winnti Group (Welivesecurity(ESET), 2020/05/21 11:30)
The notorious APT group continues to play the video game industry with yet another backdoor
https://www.welivesecurity.com/2020/05/21/no-game-over-winnti-group/
⇒ https://malware-log.hatenablog.com/entry/2020/05/21/000000_1
■2022年
◆APT41 World Tour 2021 on a tight schedule (Group-IB, 2022/08/18)
https://blog.group-ib.com/apt41-world-tour-2021
⇒ https://malware-log.hatenablog.com/entry/2022/08/18/000000_7
■2023年
◆ステルス性増す中国のサイバースパイ:検知回避の戦術がさらに進化 (Mandiant, 2023/07/18)
https://www.mandiant.jp/resources/blog/chinese-espionage-tactics
⇒ https://malware-log.hatenablog.com/entry/2023/07/18/000000_9
【公開情報】
■2013年
◆Winnti. More than just a game (SECURELIST, 2013/04/11) ☆☆
https://securelist.com/winnti-more-than-just-a-game/37029/
⇒ http://malware-log.hatenablog.com/entry/2013/04/11/000000_6
◆Backdoor.Winnti (Symantec, 2013/04/12)
https://www.symantec.com/ja/jp/security_response/writeup.jsp?docid=2011-102716-2809-99&tabid=2
⇒ http://malware-log.hatenablog.com/entry/2013/04/12/000000_1
◆Winnti Backdoor Created with Aheadlib to Mimic Legitimate System Library (Softpedia, 2013/05/10)
https://news.softpedia.com/news/Winnti-Backdoor-Created-with-Aheadlib-to-Mimic-Legitimate-System-Library-352240.shtml
⇒ http://malware-log.hatenablog.com/entry/2013/05/10/000000_2
■2020年
◆國內重要企業遭勒索軟體攻擊事件調查說明 (台湾政府, 2020/05/15 13:45)
重要な国内企業に対するランサムウェア攻撃の調査の説明
https://www.mjib.gov.tw/news/Details/1/607
⇒ https://malware-log.hatenablog.com/entry/2020/05/15/000000_10
【資料】
■■■マルウェア・組織
■2013年
◆Winnti (Kaspersky, 2013/04)
https://kasperskycontenthub.com/wp-content/uploads/sites/43/vlpdfs/winnti-more-than-just-a-game-130410.pdf
⇒ http://malware-log.hatenablog.com/entry/2013/04/01/000000_1
◆Winnti Backdoor Created with Aheadlib to Mimic Legitimate System Library (Softpedia, 2013/05/10)
https://news.softpedia.com/news/Winnti-Backdoor-Created-with-Aheadlib-to-Mimic-Legitimate-System-Library-352240.shtml
⇒ https://malware-log.hatenablog.com/entry/2013/05/10/000000_2
■2014年
◆Internet Infrastructure Review (IIR) Vol.23 (IIJ, 2014/05/28)
http://www.iij.ad.jp/company/development/report/iir/023/01_04.html
⇒ https://malware-log.hatenablog.com/entry/2014/05/28/000000_2
■2015年
◆WINNTI ANALYSIS (NOVETTA)
http://www.novetta.com/wp-content/uploads/2015/04/novetta_winntianalysis.pdf
⇒ https://malware-log.hatenablog.com/entry/2016/06/20/000000_7
◆Backdoor.Winnti attackers have a skeleton in their closet? (Symantec, 2015/01/29)
https://www.symantec.com/connect/nl/blogs/backdoorwinnti-attackers-have-skeleton-their-closet?page=1
⇒ https://malware-log.hatenablog.com/entry/2015/01/29/000000_2
◆WINNTI ANALYSIS (Novetta, 2015/04/07)
http://www.novetta.com/wp-content/uploads/2015/04/novetta_winntianalysis.pdf
⇒ https://malware-log.hatenablog.com/entry/2015/04/07/000000_1
■2016年
◆Winnti Polymorphism (Symantec, 2016/12/19)
https://hitcon.org/2016/pacific/0composition/pdf/1201/1201%20R2%201610%20winnti%20polymorphism.pdf
⇒ https://malware-log.hatenablog.com/entry/2016/12/19/000000_2
■2017年
◆Winnti (NJCCIC, 2017/04/03)
https://www.cyber.nj.gov/threat-profiles/trojan-variants/winnti
⇒ https://malware-log.hatenablog.com/entry/2017/04/03/000000_4
◆Winnti Evolution - Going Open Source (PROTECTWISE, 2017/07/11)
https://www.protectwise.com/blog/winnti-evolution-going-open-source.html
⇒ https://malware-log.hatenablog.com/entry/2017/07/11/000000
◆Burning Umbrella: An Intelligence Report on the Winnti Umbrella and Associated State-Sponsored Attackers (401 TRG, 2018/05/03)
https://401trg.com/burning-umbrella/
⇒ https://malware-log.hatenablog.com/entry/2018/05/03/000000_1
■2017年
◆Exposing the arsenal and methods of the Winnti Group (ESET, 2019/10/21)
https://www.welivesecurity.com/wp-content/uploads/2019/10/ESET_Winnti.pdf
⇒ https://malware-log.hatenablog.com/entry/2019/11/21/000000_1
■■■その他
■2017年
◆JPCERT/CCが見た、標的型攻撃の実態 (久保啓司, 2017/11/28)
https://www.nic.ad.jp/ja/materials/iw/2017/proceedings/d1/d1-1-kubo.pdf
⇒ https://malware-log.hatenablog.com/entry/2017/11/28/000000_7
■2018年
◆APTマルウェアに⾒る不易流⾏ (Macnica Networks, 2018/01/25)
https://www.jpcert.or.jp/present/2018/JSAC2018_09_yanagishita-takeuchi.pdf
⇒ https://malware-log.hatenablog.com/entry/2018/01/25/000000_7
【IoC情報】
◆Winnti returns with PlugX (IoC (TT Malware Log))
https://ioc.hatenablog.com/entry/2013/04/15/000000
◆Winnti (IoC (TT Malware Log))
https://ioc.hatenablog.com/entry/2016/03/15/000000
◆Winnti (IoC (TT Malware Log))
https://ioc.hatenablog.com/entry/2016/06/20/000000
◆PipeMon (Winnti) (IoC (TT Malware Log))
https://ioc.hatenablog.com/entry/2020/05/21/000000
【図表】

Suckfly hacking tools and malware, characterized by functionality

Tracking Suckfly’s use of stolen certificates, by month
出典: https://www.symantec.com/connect/blogs/suckfly-revealing-secret-life-your-code-signing-certificates

Suckfly のライフサイクル
出典: https://www.symantec.com/connect/nl/blogs/suckfly-2?page=1

出典: https://www.itmedia.co.jp/enterprise/articles/2003/26/news072.html
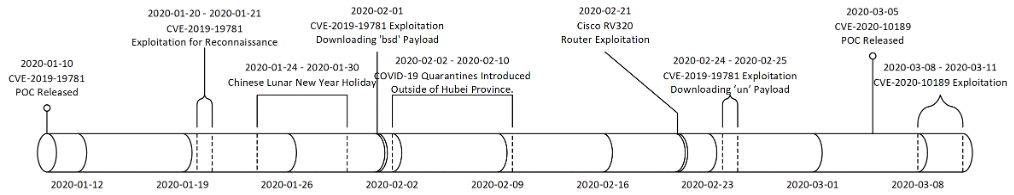
出典: https://threatpost.com/chinese-hackers-exploit-cisco-citrix-espionage/154133/


出典: https://www.zdnet.com/article/us-charges-five-hackers-part-of-chinese-state-sponsored-group-apt41/
【検索】
google: Winnti
google: Blackfly
google: Suckfly
google: Wicked Panda
google: Wicked Spider
google: APT41
google: Barium
google: Amoeva
google: Bronze Atlas
google:news: Winnti
google:news: APT41
google: site:virustotal.com Winnti
google: site:virustotal.com APT41
■Bing
https://www.bing.com/search?q=Winnti
https://www.bing.com/search?q=APT41
https://www.bing.com/news/search?q=Winnti
https://www.bing.com/news/search?q=APT41
https://twitter.com/search?q=%23Winnti
https://twitter.com/search?q=%23APT41
関連情報
【関連まとめ記事】
◆標的型攻撃組織 / APT (まとめ)
https://malware-log.hatenablog.com/entry/APT
インディケータ情報
【インディケータ情報】
■通信先
| Indicator | Description |
| job.yoyakuweb.technology | Phishing email link destination. |
| resume.immigrantlol.com | Phishing email link destination. |
| macos.exoticlol.com | Likely phishing email link destination. |
| css.google-statics[.]com | BeEF Landing and C2. |
| minami.cc | Potential BeEF - Low confidence (Linode) |
| vps2java.securitytactics.com | Malware C2 |
| 106.184.5.252 | Phishing email link destination. |
| 61.78.62.21 | Used in BeEF C2, reused Winnit Infra. |
| 139.162.106.19 | Linode - Used in BeEF C2. |
| 172.104.101.131 | Linode - Malware C2. |
| 139.162.17.161 | Linode - Used in BeEF C2. |
| 133.242.145.137 | Linode - Used in BeEF C2. |
| 106.185.31.128 | Linode - hosting BeEF landings. |
以上は「Winnti Evolution - Going Open Source」より引用
https://www.protectwise.com/blog/winnti-evolution-going-open-source.html
■通信先(C&Cサーバ)
| IPアドレス | ポート |
|---|---|
| 160.16.]243.129 | 443 (HTTPS) |
| 160.16.243.129 | 53 (DNS) |
| 160.16.243.129 | 80 (HTTP) |
| 174.139.203.18 | 443 (HTTPS) |
| 174.139.203.18 | 53 (DNS) |
| 174.139.203.20 | 53 (DNS) |
| 174.139.203.22 | 443 (HTTPS) |
| 174.139.203.22 | 53 (DNS) |
| 174.139.203.27 | 53 (DNS) |
| 174.139.203.34 | 53 (DNS) |
| 174.139.62.58 | 80 (HTTP) |
| 174.139.62.60 | 443 (HTTPS) |
| 174.139.62.60 | 53 (DNS) |
| 174.139.62.60 | 80 (HTTP) |
| 174.139.62.61 | 443 (HTTPS) |
| 61.195.98.245 | 443 (HTTPS) |
| 61.195.98.245 | 53 (DNS) |
| 61.195.98.245 | 80 (HTTP) |
| 67.198.161.250 | 443 (HTTPS) |
| 67.198.161.250 | 53 (DNS) |
| 67.198.161.251 | 443 (HTTPS) |
| 67.198.161.252 | 443 (HTTPS) |
以上は「「WINNTI」、C&C通信にGitHubを悪用」より引用
http://malware-log.hatenablog.com/entry/2017/03/30/000000
■使用マルウェア
Backdoor.Nidiran (侵入時)
HackTool password thief for reconnaissance and lateral movement within victim networks
■使用脆弱性
| CVE-2014-6332 | OLE における任意のコードを実行される脆弱性 |
